Security as Code Protects Rapidly Developing Cloud Native Architectures

Enterprises are increasingly going beyond lift-and-shift migrations to adopt cloud native strategies — the approach of developing, releasing and maintaining applications, all within cloud environments. According to Gartner, more than 95% of new digital initiatives will be conducted on cloud native platforms by 2025.
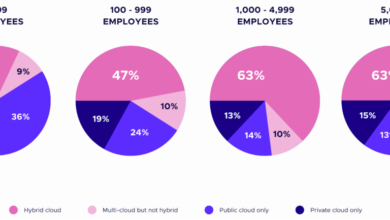
As enterprises dial up the focus on cloud native functionality, they’re moving away from manual click-Ops approaches to adopt automation that enables higher velocity and better manages increasing cloud complexity and scale. HashiCorp’s State of Cloud Strategy Survey shows that 81% of enterprises are already multicloud or plan to be within a year. Of those who have adopted multicloud, 90% say it works for them.
There’s a familiar problem amid all this adoption, one that’s plagued the entire industry for years: Traditional security workflows can’t keep up. They were never designed to support a paradigm where the architecture is represented as code that can change several times a day. The velocity and scope of change of today’s cloud native architectures cause security teams to struggle.
Embracing automation is the only viable approach for security teams to support this new paradigm. Developers have leaned on Infrastructure as Code (IaC) to build these cloud native applications on a large scale, even in complex environments. Security as Code (SaC) also leverages automation to intelligently analyze and remediate security and compliance design gaps, even as context changes. It’s the missing piece that completes an enterprise cloud environment.
HashiCorp’s survey shows a whopping 89% of respondents see security as a key driver of cloud success. Cloud-service providers recognize their customers’ challenges and are making investments in security to mitigate them.
Infrastructure automation tools are a catalyst for boosting operational efficiency in development, and the same is true for security. Automation helps optimize cost and scale operations. SaC ensures these applications are built right the first time, rather than security teams rushing to put out fires after they’re deployed. Empowering security teams to codify security best practices, and enforce them autonomously, allows them to focus on the strategic work of building standards that provide the necessary guardrails for developers to move with velocity. The future of SaC should be a corollary of IaC adoption, which is growing.
SaC helps both security and development teams operate autonomously, share responsibility, and collaborate more effectively in delivering secure products and features at the speed required by today’s business landscape. SaC is the only way that we can ensure security keeps up with the rapid pace of cloud native development.
How We Got Here
Modern application architectures have increased scale and complexity, completely outpacing traditional security methods, which can’t offer adequate protection in today’s landscape. These architectures are defined in IaC languages like Terraform and often span more than 100,000 lines of code that change frequently. This has allowed development teams to rapidly evolve the architecture, deliver infrastructure in an agile manner, and build architectures at an unparalleled scale and velocity.
These developers are increasingly empowered to choose their cloud providers, feature capabilities and tech stacks to rapidly deliver on customer needs. With all the choices developers are empowered to make, applications live in heterogeneous environments that are difficult to manage. If we were to measure the average entropy of an application architecture based on the interconnectedness of components, the curve would be exponential. Add in the false positives and lack of actionable, achievable and applicable feedback, and the impact on developer productivity is huge. This is especially detrimental at scale, and when time to market is a critical business objective.
Now consider the breadth of the community that’s creating these complex architectures. The Cloud Native Computing Foundation (CNCF) reports that there are 7.1 million cloud native developers — more than two and a half times the population of Chicago.
Multicloud strategies, diversity of cloud-feature capabilities, disparate tech stacks and an enormous base of developers combine to make security an incredibly complex undertaking. Functionality is prioritized, and often the security guardrails we need are not calculated in that developer freedom.
Why SaC
Traditional security measures simply can’t match the scale of today’s cloud native architectures, and enterprises recognize this issue. One report shows that nearly 70% of organizations believe their cloud security is only “somewhat mature,” and 79% aren’t sure they enforce policies consistently.
The answer is SaC, because it solves the most-pressing business challenges.
Say you need to deliver a unique solution for a fleeting business opportunity. Often, security considerations slow down the time to market. With SaC, instead of being an inhibitor, security becomes an accelerator. SaC provides the developers with flexible guardrails that let them operate autonomously with velocity. Developers can evolve their feature capabilities without having to slow down for security and potentially miss the window of opportunity.
SaC comes to the rescue when technology needs change, like modernizing your tech stack to pay off tech debt and adopt new capabilities. It also allows you to rapidly evolve security practices when your threat landscape changes because your business is increasingly being targeted. Enterprises struggling with compliance at scale can alleviate those challenges by leveraging SaC to automate compliance workflows to reduce the time and cost of becoming compliant.
McKinsey saw the promise of SaC as the best “and maybe only” path to securing cloud native architectures more than a year ago. In addition to being the next logical step of IaC and operating at the scale and pace of innovation with security baked in, SaC creates transparency in security design, and consistent, repeatable and reusable representations of the security architecture.
What SaC Enables
We’re already seeing the payoff. Opening up our SaC framework is the feature our customers ask for the most. It’s allowed resource-constrained security teams to stop putting out fires and elevate their strategy, leveraging automation to do the tedious work. Our customers have reported a 70% reduction in security design review time and 40% reduction of cost in delivering security design by automating design validation using SaC.
SaC is also the key to unlocking collaboration, autonomy and shared responsibility across development and security teams, enabling the DevOps and DevSecOps cultures that organizations want to adopt.
This is increasingly a priority, as 62% of organizations have a DevSecOps plan or are evaluating use cases, and 84% believe getting the right data and tools to developers is key to enabling DevSecOps, according to ESG Research. As modern application development evolves, SaC is the accelerator that allows security to keep pace with everything else.
Envisioning a Modern Security Practice
Developers have been unleashed to innovate as fast as possible, using whatever tools and cloud environments they wish. The only way to have security keep up with them is to identify best practices at the policy level, agnostic to the technology stacks these developers choose. Automation, powered by SaC, turns that from a dream to reality.
We can use SaC to fit into developers’ workflows and democratize security for them. This completely changes the dynamic of how developers and security interact. Ten years from now, the traditional workflows that rely on Word documents, Excel spreadsheets and Visio diagrams will be a thing of the past. Developers will have an increased responsibility for security, with collaboration making those efforts stronger. When security is defined as code, developers can easily change a security architecture to better meet their requirements.
Shifting to SaC allows enterprises to make security a driver of their velocity and agility. Automation improves security from reducing human error, to eliminating scaling challenges so security can keep pace with development, to providing richer security policies.
With SaC, we finally have a way to quickly make changes that deliver repeatable outcomes at the same speed as application development. As cloud native architectures become more prominent, this is the only way security can keep pace.
YOUTUBE.COM/THENEWSTACK
Tech moves fast, don’t miss an episode. Subscribe to our YouTube
channel to stream all our podcasts, interviews, demos, and more.