More Threats & Prioritization Issues

The 2023 vendor surveys arriving this quarter paint a picture of a cybersecurity landscape under attack, with priority issues affecting deployment, alert response, and exposed vulnerabilities. Most organizations express confidence in their current status and budgets, but also expect to experience at least one data breach in 2024.
This picture comes from an analysis of specific statistics and by reading between the lines in reports from 1Password, Cisco, CrowdStrike, Flashpoint, Google Threat Analysis Group/Mandiant, NetScout, Pentera, and Sophos. This article details two major findings from the report: five major cybersecurity threats and prioritization problems. After covering these findings, we will also briefly provide an overview of the reports themselves.
But first, here are five key cybersecurity takeaways to consider from the reports:
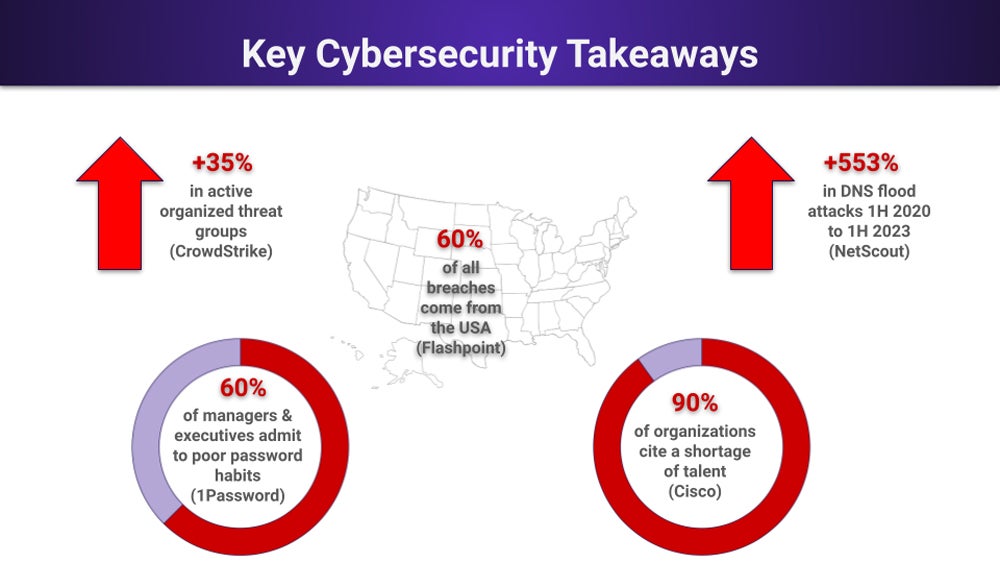
5 Major Cybersecurity Threats
Huge numbers of vulnerabilities and attackers exist and no organization can defend against all of them equally well. Fortunately, vendor surveys identify five key cybersecurity threats to watch for in 2024: compromised credentials, attacks on infrastructure, organized and advanced adversaries, ransomware, and uncontrolled devices. Read on for more details on these threats or jump down to see the linked vendor reports.
Compromised Credentials
Compromised identities from phishing, info stealers, keyloggers, and bad password habits provide the entry point for most ransomware attacks and data breaches. The vendor reports show that most attackers want credentials, most malware development is in credential-stealing software, and the market for stolen credentials is booming:
- Cisco: Found 54% of organizations experienced a cybersecurity incident; and of those incidents, 54% involved phishing and 37% involved credentials stuffing.
- Sophos: Noted that 43% of all 2023 malware signature updates are for stealers, spyware, and keyloggers often used to steal credentials from devices.
- CrowdStrike: Detected significant signs of credentials theft:
- 76% YoY increase in victims named on eCrime dedicated link sites.
- 20% increase accesses of specific organizations advertised.
- 583% increase in Kerberoasting [password hash cracking] attacks.
Attackers can compromise credentials because of extensive user password problems throughout most organizations; however, a number of security solutions provide credentials protection for both basic and advanced needs.
User Password Problems
Although these data points illustrate the magnitude of the problem, they don’t explain why credential theft and credential stuffing works. 1Password reveals that most employees, especially managers, use poor password practices such as “reusing passwords or neglecting to reset the IT-selected defaults.”
Specifically, the password problems that the report reveals are:
- 61% of [all] employees use poor password practices.
- 64% of managers and higher admit to poor password practices.
- 23% use identical passwords or follow a similar pattern.
- 13% maintain access to company tools or resources after leaving the organization.
- 9% share credentials for work tools with people outside the company.
Credentials Protection
Despite the increase in attacks, you can deploy many different tools and techniques to protect credentials. First, all organizations need to improve, enforce, and test their password policies not only against complexity and reuse, but also against private and public password breach databases. These steps take some time, but cost no money.
Additional security all organizations should consider for a modest investment include:
- Active directory security: Guards the password storage and management system against attack for Windows, Azure, and other equivalent identity management systems.
- Identity and access management (IAM): Helps improve management of users, single-sign-on (SSO), and more in Active Directory through automated workflows.
- Password manager: Stores passwords securely, enforces quality, permits safe internal and external sharing, and ties into HR software for effective off-boarding of users.
- Privileged access management (PAM): Improves discovery, procedures, storage, just-in-time deployment, monitoring, and control of privileged access.
- Multi-factor authentication: Protects stolen credentials against use by requiring more than a simple username and password combination for access to resources.
More sophisticated organizations can further protect identity with investments in tools such as:
- Application programming interface (API) security: Guards against attacks using program-to-program communication protocols.
- Risk-based analytics: Considers the level of risk as the context for the level of permission needed to access systems, applications, and data.
- Passwordless authentication: Eliminates passwords in favor of other types of authentication such as passkeys, SSO, biometrics, or email access.
- User and entity behavior analytics (UEBA): Monitors behavior of users, hardware, and network traffic to detect and potentially block abnormal and malicious activity.
- Zero-trust: Treats each access as a separate evaluation for permissions and enables granular levels of access for users, networks, applications, data, and systems.
Infrastructure Attacks
Attacks on infrastructure seek pure disruption, an angle for extortion, or peripheral benefits ranging from advantages in videogames to cover for ransomware activity. Vendor reports note huge volume of attacks on local and public infrastructure, such as:
- CrowdStrike: Monitored hacktivist and nation-state distributed denial of service (DDoS) attacks related to the Israli-Palestinian conflict, including against a US airport.
- NetScout: Observed 13,142,840 DDoS attacks, including:
- 104,216 video gaming enterprise attacks.
- 20,551 gambling industry attacks.
- 50,000 DDoS attacks on public domain name service (DNS) resolvers.
- 553% increase in DNS Flood attacks from 1H 2020 to 2H 2023.
DDoS attacks on single networks or websites render them unavailable, but DDoS attacks on DNS resolvers bring down all networks and websites using that DNS resource. Netscout identifies two key DDoS issues to stopping attacks; however, there are also a range of infrastructure protection controls that help to protect DNS and other critical functions.
2 Key DDoS Issues
NetScout identifies two key issues to defeating DDoS attacks: a sophistication gap and outgoing DDoS attacks from company infrastructure. The sophistication gap presents security professionals with the dilemma where “on one end, advanced attackers employ custom tools and cloud infrastructure; on the other, some still use basic, often free services.” Defenders need the tools and the skill to block the entire spectrum of attacks.
Outgoing DDoS attacks originate within corporate infrastructure and can lead to a company being placed on denylists and blocked. Unmanaged internal DDoS attacks can affect company reputation and ignore the fact that a large number of internal devices are showing signs of compromise. Company instructions to keep hands off internal network traffic leads to internet service provider (ISP) suppression of only 1% of the 100,000 monthly outgoing DDoS attacks.
Infrastructure Protection
Defense against DDoS and DNS attacks starts with effective network security architecture. Create redundant systems, hidden from casual access, and protected by load balancing and layers of defense to manage traffic surges until deploying other defenses. Defense can be further improved using:
Organized Adversaries
Nation-state, hacktivist, and organized criminal organizations continue to increase in number, capability, and impact. The vendor reports analyzed trends and found:
- Cisco: 62% of companies highlighted external actors as the biggest threat versus 31% for internal actors; a huge shift from 2023, which saw the threats as equal.
- CrowdStrike: Tracked significant increases in organized adversary activity:
- +34 new adversary groups (+18% of named groups, +35% active).
- +60% year over year increase in interactive (expert guided) intrusion campaigns.
- Attackers began to deliver malware to users through legitimate and common IT support tools such as ConnectWise ScreenConnect.
- Google/Mandiant: Analyzed zero-day exploits by adversaries from 2023 and found:
- 50% increase in exploited zero-days, to 97.
- 60% of all mobile and browser zero-days are exploited by spyware vendors.
- Vendors reduced common vulnerabilities, so attackers shift targets to third-party components (Linux utilities, etc.) and software libraries to attack the supply chain.
- Sophos: Observed changes in attacker behavior in response to improved defenses:
- Adopted vulnerable or malicious drivers once Windows blocked macros.
- Deployed malvertising and SEO poisoning to evade detection tools.
- Used active multi-email engagements after effective phishing screenings.
No specific tool exists to defend specifically against nation state attacks, ransomware gangs, or hacktivists. Instead, apply defense in depth, provide employee cybersecurity training, and use threat intelligence platforms to provide general protection and educate both non-technical and security teams about the latest threats.
Ransomware & Data Theft
Organizations worldwide continue to feel the pain of ransomware attacks, although many ransomware gangs may be shifting to extortion over data theft instead of encrypted data. The vendor surveys report that:
- Cisco: Analyzed that 35% of all attacks in 2023 were ransomware.
- CrowdStrike: Observed politically affiliated ransomware attacks against Israel.
- Google/Mandiant: At least four ransomware gangs exploited zero-day vulnerabilities.
- Sophos: Focused their report on small and medium business (SMB):
- 70% ransomware attacks targeted SMBs.
- > 90% of attacks reported by customers involve data or credential theft.
- Flashpoint: Gathered statistics on disclosed ransomware and data breaches:
- +84% global growth year over year in ransomware attacks.
- +34.5% globally, +19.8% US for data breaches for 2023.
- +30% data breaches and +23% ransomware for the first two months of 2024.
- 60% of all breaches come from the USA.
- 19.3% of all data breaches came from the MOVEit vulnerability, CVE-2023-34362, including breached third-party data disclosures.
- > 54% of all data breaches come from ransomware attacks in manufacturing, healthcare, government, financial, retail, and technology industries.
Despite the continuing surge in ransomware attacks, many vendors provide effective solutions to detect, slow, and even block ransomware or data theft attempts before they become crippling events.
Ransomware & Data Theft Protection
Ransomware and data breaches rely primarily on vulnerabilities exposed to the internet, phishing, and the endpoint. All organizations should at least deploy basic security tools to monitor endpoints and secure access points, such as:
- Antivirus (AV): Provides the most basic malware protection on the endpoint to block known malicious software and protect against basic attacks.
- Email security tools: Screens emails and attachments for known malware, malicious URLs, and SPAM before delivery to the end user.
- Host based and other firewall types: Filter traffic into the network or at the endpoint for malicious URLs, known malware, and other types of attacks.
- Secure remote access: Enables encrypted connections between internal network resources and remote users using a variety of methods.
More advanced security tools can incorporate artificial intelligence (AI) or machine learning (ML) to provide automated recognition and remediation for threats. However, also consider deploying specialized tools or tools with expanded capabilities, such as:
Unmanaged Devices
Although organized adversaries continue to launch increasingly sophisticated attacks, most succeed by locating unmanaged and unprotected devices that can access the network or other key assets. Unmanaged devices include a combination of corporate devices without strong policy enforcement, personal devices used for work, unmonitored cloud infrastructure, and obsolete devices no longer maintained. Vendor research specifically finds that:
- 1Password: Documents the meager control of software and personal device access:
- 92% of company policies require, but 59% enforce IT approval for software.
- 34% of workers use unapproved applications or software.
- 17% of workers work only on personal or public computers.
- Cisco: Notes the common access of personal devices and unmanaged cloud hazards:
- 43% of employees use unmanaged devices to access corporate networks.
- 20% of employee time is spent on company networks.
- 27% of all attacks mine crypto currencies, usually on unmonitored cloud systems.
- CrowdStrike: Observes the top attack vector in 2023 and predicts 2024’s targets:
- Unmanaged network appliances (edge gateway, firewall, virtual private network/VPN) remain the most observed initial access vector exploited in 2023.
- Attackers will target network peripheral devices: network attached storage (NAS), backup storage, telephones, network equipment, and end-of-life assets.
- Pentera: Focuses on the top breach origins cited by enterprise clients:
- 60% remote devices.
- 54% on-prem infrastructure.
- 50% cloud targets.
- Sophos: Finds that unprotected devices are the primary entry point for SMB attacks.
Some unmanaged devices can’t support installed technical controls, and companies often won’t install controls on employee devices. Yet, different security products can still provide defensive measures for unmanaged devices.
Unmanaged Device Defense
Many security tools help to protect against unmanaged devices, but perhaps the first step would be to authorize IT to lock down devices and enforce the requirement for IT to grant permission for all software installations. This simple step makes malware installation more challenging and compliments by other tools that either manage assets or monitor traffic, such as:
- IT asset management (ITAM): Identifies, tracks and manages devices in the organization to track software licenses, manage updates, and detect anomalies.
- Intrusion detection or prevention systems (IDS/IPS): Monitors network traffic for known malicious packets, attack patterns, and other indicators of compromise.
- Network access control (NAC): Checks device status and authorizes users attempting to access the network; can quarantine devices that need remediation.
- Network monitoring: Tracks behavior, traffic, and health of local and cloud network components for signs of failure and indicators of malicious compromise.
- Segmentation or micro-segmentation: Segregates the network and can control user, application, and device access in fine detail between segments.
More sophisticated organizations can apply more robust security, such as:
- Cloud security: Deploys cloud-native or cloud-specific security to monitor and protect cloud infrastructure and assets against attack.
- Internet of Things (IoT) security: Provides protection for peripherals and devices that can’t support on-device security protection (antivirus, etc.).
- Secure service edge or secure access secure edge (SASE): Expands security beyond the local network to secure remote and cloud resources.
Cybersecurity Preparedness: A Prioritization Problem
Organizations plan to be secure, yet breaches still occur. It’s always tempting to blame budgets, but most CISOs feel confident about their budgets and have already deployed significant resources. Unfortunately, the vendor surveys reveal that installed tools tend to overload teams already struggling to fill positions, and many vulnerabilities remain unfixed.
Many vendors attempt to address the labor issue with AI or ML enhanced automation. Yet, the prioritization problem will likely persist until vendors provide more transparency for vulnerabilities and organizations practice integrated risk management to tie priorities to the most significant impacts to the business. Let’s examine the funding, alerts, talent shortages, and unaddressed vulnerabilities in more detail.
Funded Cybersecurity Programs, But Still Incomplete
Regarding budgeting, the vendor reports show relative strength:
- Cisco: Surveyed a broad number of businesses around the world and found:
- 97% planning to increase spending.
- 80% feel moderately to very confident in defense.
- Pentera: Focused on large enterprise CISO’s with a minimum of 1,000 employees:
- 53% report decreasing or stagnating 2024 IT security budgets.
- $1.27 million per year for the average IT security budget.
- 51% recorded breaches within the last 24 months.
- 1Password: 24% of surveyed SMB describe budgets as inadequate.
So while many large companies are flat or cutting back, the average company plans to increase spending and claims to be confident. Even with budget-conscious SMBs, more than three out of four identify their budget as adequate. Yet, despite some confidence, most security managers also expect failure:
- 1Password: 79% of security pros don’t feel their security protections are adequate.
- Cisco: Found similar sentiments from managers and explored breach details:
- 73% expect business disruption in the next 12-24 months.
- 52% said previous breaches cost their organization at least US$300,000.
- 12% said previous breaches cost US$1 million or more.
Breach damages of $300k to $1 million may be within the risk tolerance for some, and many may expect to recoup damages from cybersecurity insurance. Still, the challenge of restraining the damages from an incident to policy limits faces the significant challenges we cover below.
Overloaded Alerts
1Password found that 32% of their surveyed security professionals switched security tools or vendors in the past year to ones that provide more complete end-to-end solutions. The motivation for this switch comes from the average number of tools and alerts already in place:
- 1Password: Probed security responsiveness:
- 69% are at least partly reactive.
- 61% are pulled in too many conflicting directions.
- Cisco: Explored the number of security solutions in the security stack:
- 67% have 10+ specialty security solutions.
- 25% have 30+ specialty security solutions.
- 80% admit multiple solutions slow detection, incident response, and recovery.
- Pentera: Analyzed the security solutions and alerts for the best funded enterprises:
- 89% of 1,000+ employee enterprises have at least 20 security solutions.
- 21% have at least 76 specialty security solutions.
- 90% report at least 250 security events per week.
- 30% report at least 1000 security events per week.
The large number of tools generate a flood of alerts (security incident, vulnerability to patch, etc.) and pull teams in conflicting directions. Large teams might make enough progress to become proactive, but most teams remain understaffed.
Inadequate Talent
Many cybersecurity initiatives fail to progress due to inadequate staffing levels:
- 1Password: 21% are understaffed, 20% have a lack of internal knowledge or skill sets.
- Cisco: 90% cite a shortage of talent, with 46% having at least 10 open security team slots.
- Pentera: 42% don’t conduct pentests more often because of pentester availability.
Lack of staff leads to a number of issues. The most obvious mistakes lead to headline-making such as the password issues for Okta customers (2022), because staff must remain on-call 24/7. Most mistakes remain hidden risks waiting to be exploited – especially in the form of exposed vulnerabilities.
Exposed Vulnerabilities
Most security teams worry the most about zero-day attacks that strike without warning. However, far more concern should be applied to known and unaddressed vulnerabilities:
- 1Password: 24% have difficulty staying up to date on patch/update cycles.
- Flashpoint: Investigated the severity and exploits of vulnerabilities:
- 52% of vulnerabilities rate high to critical.
- 35% of vulnerabilities have publicly known exploits.
- Pentera: Probed how security professionals prioritize which vulnerabilities to prioritize:
- 34% based on business impact.
- 40% based on CVSS scores.
- 44% based on vendor risk scoring.
Almost one out of four organizations struggle to keep up with patching, which starts to sound acceptable until an organization considers vendors and suppliers. Suddenly, the specter of third-party risk becomes more pronounced when it becomes probable that at least part of every supply chain will have exposed vulnerabilities.
Additionally, two out of five prioritize based on formal vulnerability ratings, but Flashpoint notes that over 100,000 vulnerabilities lack a tracking ID number, including prominent vendors such as Apache, Google, Microsoft, and Zoho. Attackers actively exploit hundreds of these non-tracked vulnerabilities in the wild, and this doesn’t even include disputed vulnerabilities such as the ShadowRay AI framework exposure.
Penetration tests can uncover both exposed and unacknowledged vulnerabilities, but most penetration tests don’t cover a full organization.
Partial Penetration Testing
Penetration testing verifies existing controls, uncovers mistakes, and reveals exposed assets before an attacker can exploit them. Yet, Pentera finds that even well-funded organizations struggle to conduct sufficient pentests:
- 73% change systems significantly in a quarter, while only 40% pen test quarterly.
- Organizations selectively test infrastructure:
- 49% test cloud resources.
- 49% test external facing assets.
- 44% test priority internal network assets.
- 15% test individual applications.
- 31% conduct pentesting to assess the potential damage of a successful attack.
When even the most funded organizations struggle, we can easily see why breaches remain common. Close to one out of three organizations conducting pentests do so retroactively as part of a breach investigation. This reveals the price to pay for exposed vulnerabilities, understaffed teams, and alert overload: always playing catchup instead of staying ahead of breaches.
About the Sources
This article pulls from eight vendor reports on 2023 trends from 1Password, Cisco, CrowdStrike, Flashpoint, Google Threat Analysis Group/Mandiant, NetScout, Pentera, and Sophos:
Bottom Line: The Current Cybersecurity Status Needs Improvement
The 2023 reports depict an acceptable, but hardly stellar, cybersecurity environment in which security professionals are almost as confident in a business disruption (73%) as in their readiness (80% moderately to very confident). Of course, labor shortages, alert overload, and exposed vulnerabilities provide excuses for breaches and reasons for breaches.
Many solutions exist, but the correct solution depends on current network architecture, existing security investments, and fit with existing strategies. Some should embrace AI to automate remediation, some should pursue platforms to consolidate alerts, and some should outsource to managed security service providers (MSSPs). To make 2024 successful, explore options now to shift your organization from reactive to prepared.
To explore the outsourcing option for security, consider reading more about managed security service providers (MSSPs).



