Why Federated SIEM is Critical for Multi-Cloud Architectures
Scattered Data Sets and Compliance Challenges
With applications and data hosted in multiple clouds, spread across different regions, and across cloud data centers, it is challenging for analysts to achieve consolidated visibility required to monitor and detect threats, gather context for investigations, and understand how to respond.
Requirements by specific countries and regions often forbid certain data to be moved from the local environment. For example, GDPR restrictions may prevent data from being exported out of the region or host country.
To overcome these hurdles, organizations often attempt to deploy a SIEM solution in each cloud and region. This is the primary mechanism that current SIEMs use to respect data sovereignty regulations. However, this means that the SIEM solution must be deployable within each cloud provider. The challenge is that while many SIEMs can ingest data from different cloud providers, they are usually tied to one primary cloud vendor in terms of deployment. In addition, even if the SIEM does support more than one provider, the security team must be trained to operate and actively manage each SIEM in each distinct cloud environment. That requires extensive training and certifications to accomplish.
Cost of Moving Data
Moving large data sets across clouds to combine and analyze data often leads to significant costs in transferring or making copies of data. Large-scale data transfers can also lead to greater risk and exposure for data loss or theft. Just as data can be spread across cloud providers, threats can also be spread across multiple providers. For security teams looking for threats, they need to see a consolidated view across the entire set of federated infrastructure. However, to consolidate the telemetry, the transfer costs charged by cloud providers when moving data from one to another cloud provider can escalate costs rapidly. In addition, some of the data being transferred may also end up replicated across multiple storage services, adding even more to the total cost of the solution.
The need to keep data distributed and the ability to deal with multiple silo requirements push SIEM deployments to a distributed model, and this is where a federated SIEM model shows its advantages.
How Federated SIEM Works
These challenges have reduced the reliability and scalability of most SOC solutions today. Part of the problem for security vendors is that their fundamental architectures must be completely rebuilt to support the one capability that can significantly improve cloud observability and threat detection accuracy across today’s enterprise cloud architectures, Federated SIEM. Federated SIEM can allow security teams to bridge the data silos, retain data for analysis locally, and investigate across toolsets that reside in their cloud, SaaS, and on-premises environments.
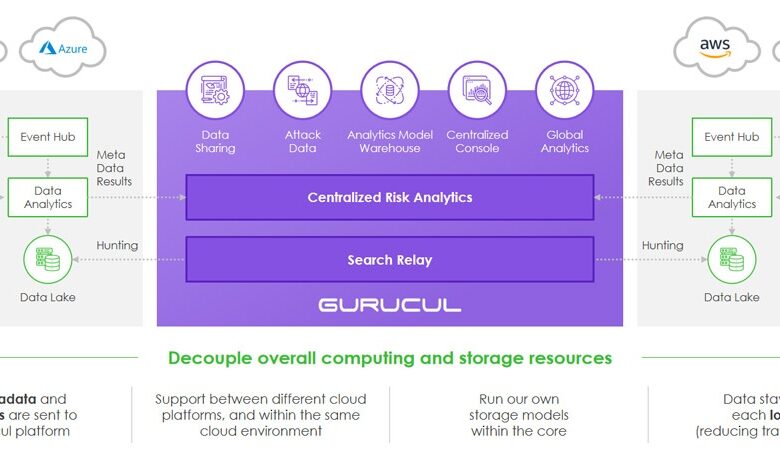
Federated Search for Consolidation
At the core of a “Federated” SIEM is the ability to perform federated search. A single search request spans all data sources across security technologies, cloud environments, data stored in Amazon S3 buckets, Active Directory, cloud-hosted human resource systems, hypervisors, Windows event logs, etc.
A federated search retrieves information from across vendor solutions and environments. It uses API integrations with third parties to perform a unified search across the data sources that are participating in the federation, and it does this without requiring cross-cloud or restricted region data transfers to a centralized SIEM. This prevents having to pivot and manually login to many different applications to collect data, apply security analytics and power investigations.