Asking the Hard Questions About Cybersecurity at Infocomm 2024 – rAVe [PUBS]
![Asking the Hard Questions About Cybersecurity at Infocomm 2024 – rAVe [PUBS] Asking the Hard Questions About Cybersecurity at Infocomm 2024 – rAVe [PUBS]](https://europeantech.news/wp-content/uploads/2024/06/PK-security-at-infocomm-780x470.jpg)
When I departed Bradley International Airport on Tuesday, the temperature was a cool 70 degrees Fahrenheit. When I landed in Las Vegas 5 hours later, it was about 700 degrees. Okay, it wasn’t 700, but it was 101. I don’t know about you, but I dread this sort of heat. But I am here for a reason: to attend Infocomm 2024 to bring my own heat, so to speak. I am here to ask some hard questions about the cybersecurity features of AV products and services. These are some of the typical security-related questions I am asking at Infocomm:
1. Is MFA (multi-factor authentication) enabled/required by default for cloud-based solutions?
2. Are all of the configuration changes and other events being logged? Where? For how long?
3. Do you have any security-related certifications, or comply with any security-related guidelines?
One of the first booths I visited was Xten-AV, a company renowned for its expertise in AV cybersecurity. Here, I had the opportunity to speak with Akshay Singh, the customer service manager. He confirmed that the company requires MFA by default to enter its cloud-based platform, a testament to its commitment to robust security measures. However, they are still working on implementing event logging, a feature that is in high demand among their clientele.
Logging is a double-edged sword. On the one hand, it’s important to know how a device has been configured, what other changes have been made to the project or the program, and by whom and when. This is often known as an audit trail. However, by keeping a log record of all of these changes or events, a malicious actor who gets ahold of the logs could also determine how and when would be the best time to attack. Or the hacker could also change the log file, deleting malicious activity. Thus, access to the log files themselves needs to be limited and secured so the files can maintain their integrity.
My next destination was the thinklogical (lowercase t) booth, where I had the privilege of conversing with Richard Cooper, VP of sales. Richard introduced me to thinklogical’s unique ‘secure, high-performance KVM (keyboard, video, mouse) extension and switching solutions.’ He showcased a touchscreen controller that allows users to select a video source through drag and drop, a feature that enhances security by preventing Adversary-In-The-Middle attacks. Most notably, thinklogical has the capability to switch video between multiple domains or classifications, a feature that is of utmost importance in Military Applications.
Richard from thinklogical also confirmed that the company indeed has event logging and told me the log files are stored locally in the matrix. If a person wants to retrieve the log files, they need physical access to the device, typically used in a secure environment. Richard explained how the data (video) is never stored “at rest,” there is no way to “look” at the live video, and there is no thumbnail preview, which makes it more secure by design. They also have a special modification to the fiber connector so there is no backchannel; the data only flows one way, also known as a data diode. This is different from other HDMI or fiber extenders that allow bidirectional control. All of these features are what allow thinklogical to get military certifications like JITC and TEMPEST.
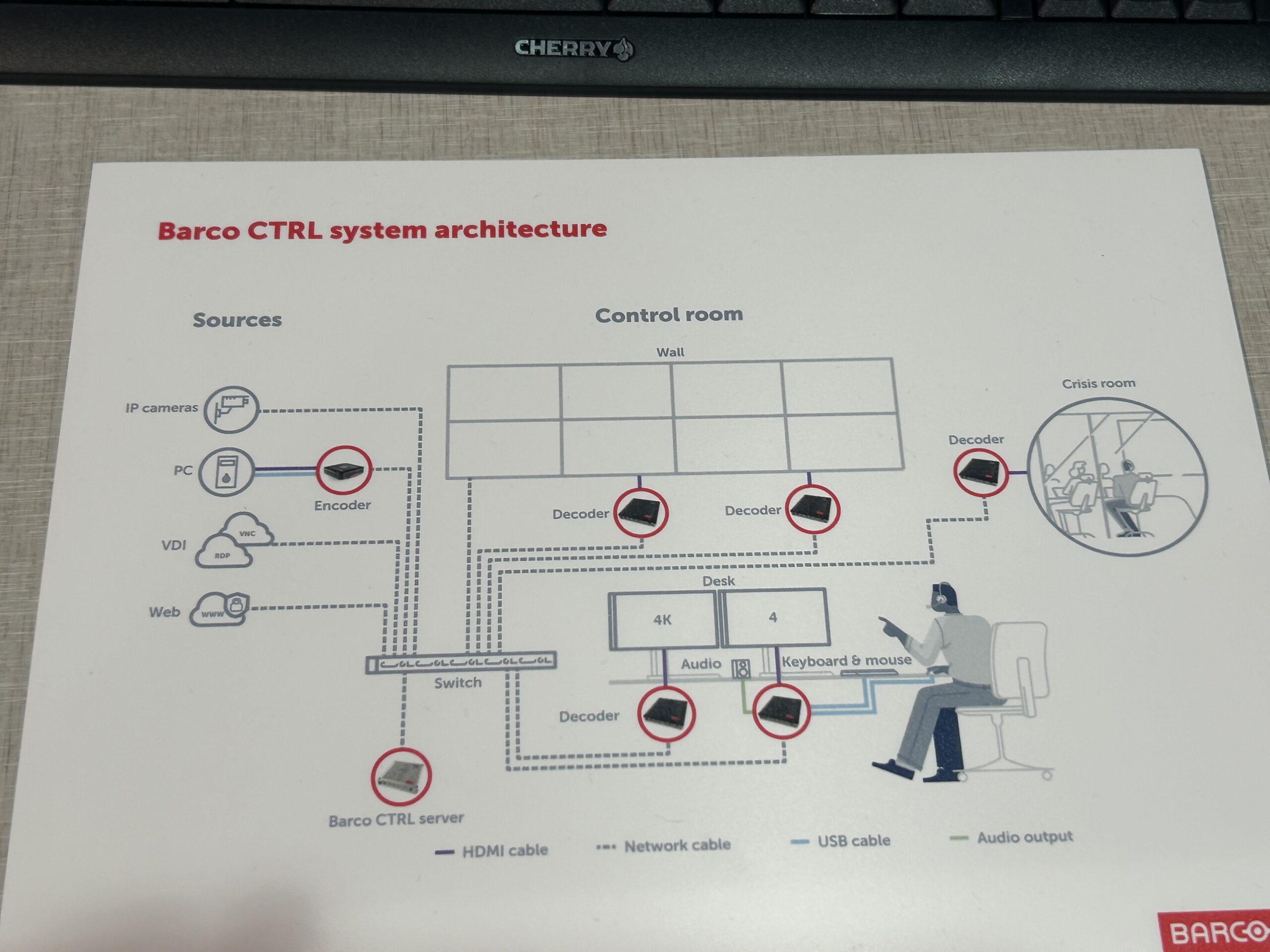
Next, Shane Myers and his coworkers at Barco demonstrated some good security features in their CTRL system architecture. Every Barco device is shipped with a certificate of authority (CA) that proves it is a genuine Barco device, but that CA is only used for the first boot-up. After that first boot, the control server generates another unique certificate of authority (CA), and as more devices are added, additional unique CAs are generated and assigned. Barco customers can add their own unique CA if they choose. This unique CA per device feature provides a mTLS (mutual TLS) connection between devices. This means that one Barco AV-over-IP system can not decrypt the traffic from another system. For instance, if the decoders were swapped or a malicious actor purchased a decoder from the secondary market, it wouldn’t work.
This differs from other AV-over-IP solutions in different booths, where a bad actor can easily add a rogue decoder to a network and view any video stream. Barco also features full logging; the logs are stored locally, or a secure TLS connection can access them. Barco hopes to achieve JTIC certification soon, and they also comply with IEC 62443. This Wikipedia entry says, “IEC 62443 is an international series of standards that address cybersecurity for operational technology in automation and control systems. The standard is divided into sections and describes technical and process-related aspects of automation and control systems cybersecurity. It divides the cybersecurity topics by stakeholder category/roles, including the operator, the service providers (service providers for integration and maintenance), and the component/system manufacturers. The different roles each follow a risk-based approach to prevent and manage security risks in their activities.”
Lastly, Barco complies with the ISO 27001 standard, which is more about the overall organization and product development cycle. ISO says, “ISO/IEC 27001 is the world’s best-known standard for information security management systems (ISMS). It defines the requirements an ISMS must meet. The ISO/IEC 27001 standard provides companies of any size and from all sectors of activity with guidance for establishing, implementing, maintaining and continually improving an information security management system. Conformity with ISO/IEC 27001 means that an organization or business has put in place a system to manage risks related to the security of data owned or handled by the company and that this system respects all the best practices and principles enshrined in this International Standard.”
Barco and thinklogical both answered all of my security questions perfectly. While Barco is still working to obtain some of the security certifications, the company knew exactly what it needed to obtain them, and it is working hard towards those goals. Xten-AV and some other products on the floor had some basic security features like MFA or encryption, but lacked the bigger security certifications needed for military applications.
Stay tuned for more articles as I keep walking the Infocomm show floor and asking the hard (or maybe not so hard) questions.



