Adopting a holistic approach to cybersecurity
In recent years, oil and gas and other energy-related assets have become a primary target of cyber attackers. The most well-known example occurred in 2021, when a ransomware attack shut down the Colonial Pipeline and temporarily prevented fuel delivery to a large part of the U.S. East Coast. The same year, Saudi Aramco reported that it was the victim of a $50-million extortion, after hackers were able to access internal data.
With the frequency and sophistication of these attacks increasing, organizations—from oil and gas producers to pipeline operators to utilities—must be prepared to operate in an environment where attacks are not just probable but inevitable. Ever-increasing automation and digitalization only exacerbate cyber risks. Tightening regulations in the face of rising threats also poses challenges for the industry. The introduction of NIS 2 in the European Union (EU), for instance, places new reporting requirements on firms in the oil and gas sector.
A mature and robust cybersecurity strategy is now a key competitive advantage for energy companies. In this article, we discuss what a holistic cybersecurity approach looks like and outline practical steps that companies can take to improve cyber resiliency.
CONVERGENCE OF IT AND OT
The convergence of IT and OT has fundamentally transformed how industrial organizations think about cybersecurity.
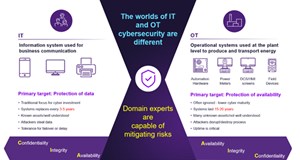
Traditionally, these two technology areas have been operationally separate, using different platforms with different objectives and characteristics. IT systems manage the core tasks of a business. They are typically updated several times a year, easy to outsource and rapidly being moved to the cloud in most enterprises. Fig. 1 below illustrates this difference.
OT systems represent the core assets used to conduct the true business of the enterprise. This means the production assets, including turbines, compressors, power generation equipment, automated production machinery and supporting systems. The critical requirement for such assets is availability (unlike IT systems, where confidentiality takes the highest priority). In energy markets, especially, being offline when contracted to deliver power or oil and gas is a very serious matter.
For this reason, OT assets are treated as a separate class of technology and thus require their own management approach and cybersecurity strategies. Simply applying IT methods to OT will not deliver the desired outcomes. In addition, OT assets tend to have much longer lifecycles than IT systems, and they usually are less cyber-mature than equivalent IT systems. They are also more accessible now than in the past, because they are more connected.
Convergence makes businesses much more efficient and responsive to changing needs. However, it could make OT assets visible to external bad actors, if protection policies and measures are not adequately designed and implemented. In the past, threats required physical access to the production assets—often delivered by USB sticks. Now, it is possible to enter the environment remotely, which is a significant change.
TECHNOLOGY, PEOPLE AND PROCESSES
Technology often takes center stage during industrial cybersecurity discussions—and rightfully so. Security solutions designed for OT environments—such as firewalls, intrusion detection and prevention systems and security information and event management (SIEM) tools—are essential to a comprehensive defense-in-depth strategy. However, technology implementation alone does not constitute a holistic cybersecurity approach. The human and process components are also crucial.
Organizations must foster a strong security culture by raising awareness, providing training and promoting a sense of responsibility among employees. This includes educating personnel on common cyber threats, the importance of following security protocols and the potential consequences of a security breach. Regular training and awareness programs help individuals understand their role in maintaining cybersecurity and enable them to identify and report suspicious activities.
In addition, employee responsibilities for cybersecurity within the workforce should be clearly defined. This needs to be accompanied by a structured approach to managing cyber risks, which includes conducting regular risk assessments to identify vulnerabilities and defining security policies and procedures, based on industry best practices and enforcing access controls and authentication mechanisms, Fig. 2.
Change management is also essential. OT infrastructure is not static. Updates to existing systems and new equipment installations happen frequently, which will continue to be the case, as operators look to take advantage of rapidly evolving technology. These risks are especially pronounced in the power generation landscape, which is becoming more complex and fragmented, as the move to renewables and more distributed generation accelerates.
Companies must carefully assess and test any modifications or additions to ensure they do not introduce new vulnerabilities. Documentation and record-keeping of changes and regular audits help maintain a secure and compliant environment.
Finally, incident response plans and procedures should be developed and tested regularly. Examples include establishing communication channels, defining escalation paths and conducting tabletop exercises, to enhance preparedness for potential security incidents. Ultimately, the longer it takes to detect and contain a security breach, the greater the potential impact on the asset.
THE IMPORTANCE OF OT VISIBILITY
Visibility into OT systems is a prerequisite for effective cybersecurity. After all, a company cannot protect against vulnerabilities it cannot see. Most operators are unaware of the attack surfaces within their systems and rely on isolating assets in the operational environment behind physical and digital security barriers. Potential breaches are only dealt with after they are detected. Unfortunately, by this time, it is often too late.
Many leaders view their vulnerability to cyberattacks primarily as a security concern rather than a problem related to understanding and context. However, staying ahead of cyber attackers demands a different approach and mindset.
Today’s energy ecosystem is a complex, multi-directional and interconnected mesh network. The critical challenge in safeguarding it lies in continuously monitoring, collecting, analyzing and acting on intelligence in real time. A cyber security operations center (cSOC) is critical in this regard. The recent attack on the Danish critical infrastructure and timely detection, as well as countermeasures taken by SektorCERT, illustrates the importance of early detection in limiting damage from an intrusion.
A cSOC combines a technology platform, such as SIEM, together with a team of dedicated OT cybersecurity experts. This combination enables continuous monitoring, detection and crisis support to secure energy infrastructure and industrial plants. Leveraging both human intelligence and technology, experts undertake crucial tasks, such as digital intelligence analysis and physical action, to halt cyberattacks. With deep domain expertise, they anticipate and accurately identify attackers’ tactics and work to ensure the availability and safety of the asset.
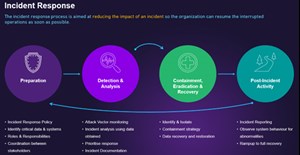
Cybersecurity teams can go beyond merely identifying anomalies by focusing on visibility and context. They can ascertain if an attack is ongoing, assess likely impacts on operations, and swiftly implement effective responses that resolve the attack with minimal disruption. A typical multi-step incidence response is shown in Fig. 3 below.
ESTABLISHING A STRUCTURED AND COMPREHENSIVE OT CYBERSECURITY APPROACH
Establishing a structured and comprehensive OT cybersecurity approach is essential to mitigating risks effectively. While the implementation process will look different for every organization, there are core actions that form the foundation of every robust cybersecurity framework, as outlined below:
Step 1 – Create awareness: The first step in a comprehensive cybersecurity strategy is creating awareness among employees and stakeholders. This involves educating individuals about the importance of cybersecurity, common cyber threats and the potential impact of a security breach. Training programs, workshops and awareness campaigns can foster a security-conscious culture throughout the organization. By making people aware of their role in maintaining cybersecurity, organizations can empower them to identify and report potential threats or vulnerabilities.
Step 2 – Conduct an assessment: A comprehensive cybersecurity assessment is needed to identify existing vulnerabilities and areas of concern. This involves evaluating the organization’s current security posture, assessing the effectiveness of existing security controls and identifying potential weaknesses in systems, processes and policies. The assessment may include penetration testing, vulnerability scanning, and reviewing security configurations. The evaluation findings will serve as a foundation for developing an action plan.
Step 3 – Identify areas for action: Based on the assessment results, organizations can identify specific areas that require action to enhance cybersecurity. This involves prioritizing risks, determining critical assets and evaluating the potential impact of security incidents. The focus is on addressing vulnerabilities and gaps identified during the assessment, such as outdated software, weak access controls or inadequate employee training. Resources can then be allocated to develop a targeted cybersecurity plan.
Step 4 – Implement measures: Once areas for action have been identified, appropriate measures to strengthen cybersecurity defenses can be implemented. Some specific examples include (but are not limited to):
- Using multi-factor authentication
- Encrypting sensitive data
- Deploying firewalls and intrusion detection systems
- Conducting regular patching and updates
- Establishing incident response processes.
It is essential to ensure that security measures are aligned with industry best practices and comply with relevant regulations and standards.
Step 5 – Monitor: Cybersecurity is an ongoing process that requires continuous monitoring and improvement. Organizations should establish mechanisms to monitor and detect potential security incidents, such as deploying SIEM systems, log monitoring and real-time threat intelligence. Regular security audits and assessments should be conducted to identify emerging threats and adapt security measures accordingly. Incident response plans should also be established and tested regularly, to ensure preparedness during a cyber security incident.
Overall, it is crucial that securing infrastructure be viewed as a journey and not simply an event. It is a continuous cycle of testing and securing the digital environment, by detecting threats and hardening systems to stay ahead of evolving cyber threats. It is most effective within a trusted ecosystem, with partners and original equipment manufacturers (OEMs) who prioritize it. Ultimately, companies are only as strong as the weakest links in their supply chains.
DIGITALIZATION AND CYBERSECURITY: TWO SIDES OF THE SAME COIN
Increasing digitalization within the energy sector comes with inherent cybersecurity vulnerabilities. As the saying goes, they are two sides to the same coin. The energy industry finds itself in a complex situation, where its infrastructure is becoming more efficient and interconnected but also more susceptible to attacks and challenging to protect.
When discussing the topic of cybersecurity in energy, it is crucial first to acknowledge that the benefits of digitalization and connectivity—when properly implemented—significantly outweigh the perceived risks. Air gapping and/or isolating industrial assets is impractical in today’s digitalized world.
Every organization must ask, “How can we effectively protect our infrastructure and stay ahead of evolving cyber threats?” In this regard, selection of technology is critical. However, cybersecurity solutions do not exist in a vacuum. They depend on every aspect of the business, its culture, working practices, core processes and, above all, the commitment and attitudes of its people.
Organizations can enhance the human factor in cybersecurity by raising awareness, providing training and fostering a strong security culture among employees. Implementing robust processes and procedures, adhering to recognized standards, and establishing effective change management and incident response practices all strengthen security posture. Additionally, deploying appropriate technological measures, such as secure network architecture, monitoring tools, and encryption protocols, ensures the protection and integrity of OT systems. By combining these elements, energy companies can enhance the cyber resilience of their OT environments and realize the full potential of digitalization.
About the Authors
Asim Zaidi
Siemens Energy
Asim Zaidi has been with Siemens Energy for over 10 years. Since 2021, he has been actively involved in developing Siemens Energy’s industrial cybersecurity service portfolio for the oil and gas, fiber and marine markets. Mr. Zaidi holds an MBA from TU Nuremberg Germany, with a Bachelor of Technology in electrical engineering.
Related Articles