Automotive Cybersecurity: A Review of 2023

//php echo do_shortcode(‘[responsivevoice_button voice=”US English Male” buttontext=”Listen to Post”]’) ?>
Automotive cybersecurity will remain the most difficult problem in the auto industry, despite much effort to create and deploy extensive solutions. New types of cybersecurity attacks are appearing to strike new vulnerabilities exposed in new software-defined vehicles (SDVs) and expanded communication technologies. This will require continuous improvements in cybersecurity technology, products and services.
The annual Upstream Global Automotive Cybersecurity Report is the best source to keep up with automotive cybersecurity trends and activities. This article is a summary of the 2024 report, which is available here in English and Japanese.
Cybersecurity overview
The 2024 report is the sixth annual version, with over 130 pages of data. Upstream has tracked 1,468 automotive-related incidents since 2010. In 2023, Upstream analyzed 295 new publicly available cybersecurity events, which is 20% of the total since 2010.
This article focuses on these key topics from Upstream’s report:
- Common vulnerabilities and exposures (CVEs) growth
- Cybersecurity incident trends
- Growing cyberattack information from social media
- Increasing diversity of cyberattack vectors
- Rising cost of cyberattacks
- Emerging impact of GenAI in cyberattacks
CVEs growth
CVEs are a measure of the weak spots where cyberattacks can be successful. The Common Vulnerability Scoring System (CVSS) was designed to provide an open and standardized method for rating CVEs. CVSS helps organizations prioritize and coordinate joint responses based on the vulnerability’s severity, time of introduction and environmental properties. Based on their CVSS score, vulnerabilities are graded as Critical, High, Medium to Low, or None.
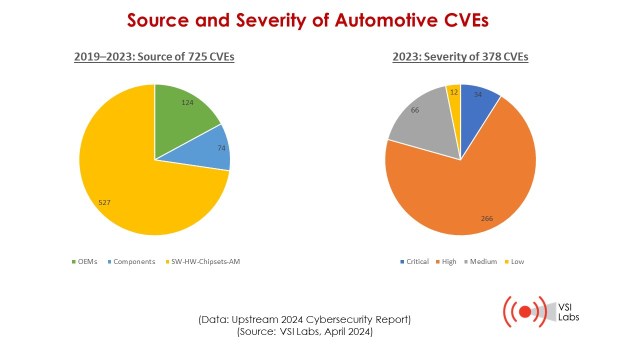
The next table shows how auto-related CVEs have grown in the last five years—from 24 new CVEs in 2019 to 378 new CVEs in 2023. Cumulative CVEs have jumped from 24 in 2019 to 725 in 2023. New CVEs added in 2023 account for over 52% of total CVEs.
|
Automotive CVE Growth |
|||||
| 2019 | 2020 | 2021 | 2022 | 2023 | |
| Auto-related CVEs found | 24 | 33 | 139 | 151 | 378 |
| Yearly growth | 38% | 321% | 9% | 150% | |
| Cumulative CVEs | 24 | 57 | 196 | 347 | 725 |
| Yearly growth | 138% | 244% | 77% | 109% | |
|
(Data source: Upstream Security, 2024 Cybersecurity Reports; Analysis: VSI Labs, April 2024) |
|||||
Upstream focused only on CVEs that directly affect the automotive and smart mobility ecosystem, such as shared mobility, mobility IoT devices and vehicle fleets. Upstream excluded CVEs that relate to generic IT hardware or open-source software components that may be used across the supply chain. Upstream tracks the source and severity of each vulnerability.
The figure below shows the sources of new vulnerabilities from 2019 to 2023 and the severity of the 378 new CVEs found in 2023. The left pie chart shows three groups of companies that introduced 725 cybersecurity vulnerabilities from 2019 to 2023, including auto OEMs, component-system suppliers (including Tier 1s) and hardware-software-chipset-aftermarket suppliers.
The CVE severity for new vulnerabilities in 2023 is summarized in the right pie chart, with four levels included. In 2023, critical and high vulnerabilities accounted for nearly 80% of total CVEs, compared with 71% in 2022. This trend highlights the importance of monitoring automotive CVEs, gaining early detection of cyberattacks and prioritizing rapid mitigation.
Cybersecurity incident trends
Automotive cybersecurity incidents continue to grow. A bigger problem is that the severity of cyberattacks is growing even faster. Upstream analyzed publicly disclosed automotive cybersecurity incidents between 2021 and 2023 based on their potential scale of impact on mobility assets. The impact included vehicles, users, mobility devices and more. Upstream categorized incidents according to four levels of impact:
- Low includes incidents that have the potential to impact under 10 assets.
- Medium covers incidents that impact up to 1,000 vehicles or mobility assets.
- High includes incidents that impact many thousands of vehicles or mobility assets.
- Massive covers incidents that have the potential to impact millions of mobility assets.
The next table is a summary of Upstream’s analysis of trends over the last three years based on the four levels of impact. The top line lists the number of incidents per year.
| Publicly Disclosed Cybersecurity Incidents by Potential Scale | |||
| Cyber incidents scale | 2021 | 2022 | 2023 |
| Number of cybersecurity incidents | 240 | 270 | 295 |
| Yearly growth of incidents | 12.5% | 9.3% | |
| Low: up to 10 mobility assets | 42.5% | 40.4% | 14.6% |
| Medium: up to 1,000 mobility assets | 36.7% | 37.5% | 35.9% |
| High: thousands of mobility assets | 19.6% | 20.6% | 44.1% |
| Massive: millions of mobility assets | 1.2% | 1.5% | 5.4% |
| (Data source: Upstream Security, 2024 Cybersecurity Report) | |||
During 2021 and 2022, high or massive incidents accounted for about 20% of total cybersecurity attacks. In 2023, the proportion of incidents with a high or massive impact doubled to nearly 50%. This shift to large-scale attacks has a major impact on the number of vehicles and mobility assets that experience cyberattacks.
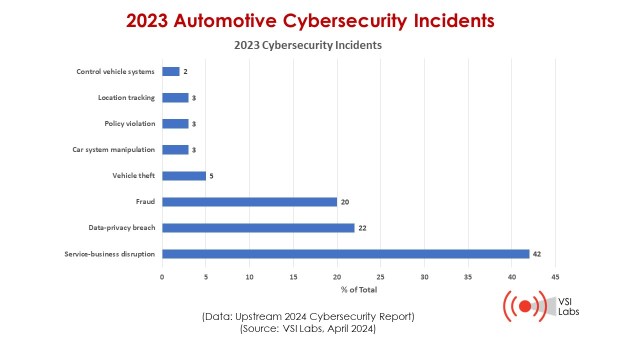
The next figure shows a breakdown of what types of automotive-related cyber incidents are most prominent. The graphs show the percentage of total cyber incidents for 2023.
Service and business disruption continues to rise, accounting for 42% of incidents in 2023, up from 40% in 2022.
Data and privacy breaches are the second-largest category, at 22% of total incidents. The desirability of such data is due to the increasing availability of credit card and related data stored in vehicle and mobility systems.
Upstream’s data show a dramatic increase in fraud-related incidents, accounting for 20% of 2023 incidents and up from 4% in 2022. One of the most popular fraud information on the deep web is mileage fix, formally known as odometer fraud. Every year, over 450,000 vehicles are sold with false odometer readings, costing U.S. buyers over $1 billion, according to NHTSA data.
Increasing cyberattack information from social media
With social media becoming a major platform for consumers and professionals, threat actors are using social media to exchange knowledge, with the potential to reach millions of people around the world in a few minutes to a few hours.
Social media’s impact on cybersecurity impact cannot be overstated. Social media’s massive reach has become a breeding ground for cyber activities. The hidden cyber content in the deep and dark web is now easily exposed and accessible to a wide audience. Based on its viral potential, social media has become a top distribution channel for malicious activities—both criminal and fraud incidents.
Moving discussions on how to hack vehicles from the deep and dark web to the open internet via social media is a disturbing trend. Auto enthusiasts and hackers can now easily share their automotive hacking discoveries with a global audience. In recent years, Facebook, TikTok, YouTube and Instagram have become key platforms for sharing automotive hacking tools, manuals, jailbreaks and hacking demos.
A prime example is the so-called “TikTok Challenge” that went viral in October 2022, leading to the nationwide theft of tens of thousands of vehicles manufactured by Hyundai and Kia. In a February 2023 press release, NHTSA called out TikTok by name, stating that a TikTok social media challenge spread nationwide and resulted in at least 14 reported crashes and eight fatalities.
Addressing the impact of cyber activities on social media requires a coordinated effort by the automotive industry, regulators and social media platforms to increase public awareness and ensure that automotive technology remains safe and secure.
Growing diversity of cyberattack vectors
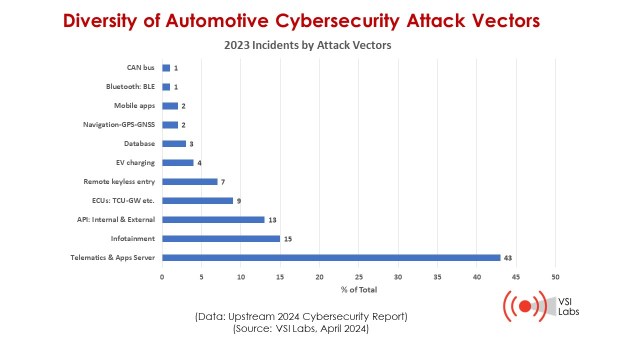
Cyberattacks became more sophisticated and frequent in 2023. They targeted multiple vehicle systems and components, as well as smart mobility platforms, IoT devices and applications. New attack methods show that any connectivity point is vulnerable to cyberattacks.
Backend servers, such as telematics and application servers, experienced a large increase in cyber incidents in 2023. Server-related incidents grew from 35% in 2022 to 43% in 2023. By exploiting vulnerabilities in backend servers, black hat actors could attack vehicles while they were on the road. Infotainment-related incidents nearly doubled—from 8% in 2022 to 15% in 2023.
Connected vehicles and smart mobility services use a wide range of external and internal APIs, resulting in billions of transactions per month. OTA and telematics servers, mobile apps, infotainment systems, mobility IoT devices, EV charging management and billing apps all rely heavily on APIs.
APIs also present significant and fleet-wide large-scale attack vectors, resulting in a wide range of cyberattacks, including personal information theft, backend system manipulation and remote vehicle control.
API hacking is cost-effective with abilities to execute large-scale attacks. It requires relatively low technical expertise, uses standard techniques and can be carried out remotely without special hardware. This is a formula for rapid future growth.
Electronic control units (ECUs) are responsible for the engine, steering, braking, keyless entry and other critical systems. Hackers try to manipulate ECUs and take control of their functions by running multiple sophisticated systems at the same time.
Wireless key fob manipulation is used by black hat actors to carry out their attacks. Wireless key fobs, which are equipped with a short-range radio transmitter, send a coded radio signal to the receiver unit. Communication between the fob and vehicle can be manipulated using devices that can intercept and relay, replay or jam the radio signal. Publicly available hacking tutorials and devices sold online without registration have made these attacks popular and easy to do.
Safe charging infrastructure is vital to the adoption of EVs. Currently, many chargers, charging infrastructure systems and related apps are vulnerable to physical and remote manipulation that expose EV users to fraud and ransom attacks. It also impacts charging network reliability.
V2X attacks are in their infancy and have not registered in cyberattacks. However, V2X cyberattacks are expected to become much more frequent in the future as C-V2X systems take off in many countries.
It is expected that C-V2X vehicles will interact with the entire environment around them, including pedestrians and cyclists, data from traffic lights and control systems at intersections, and CDA-based cooperation with other C-V2X users.
Rising cost of cyberattacks
Automotive and smart mobility cyberattacks have severe financial repercussions at multiple levels. They can lead to recalls or OTA updates, production shutdowns, ransomware payments and vehicle thefts. Additional impacts include data and privacy breaches, which can damage a brand’s reputation and customer trust and can eventually lead to large regulatory fines and diminishing revenue. With the shift toward large-scale cybersecurity incidents, future costs are expected to increase rapidly.
Upstream included a list of key financial implications from automotive cyber threats and several examples of what the cost ranges could be. This article includes one example involving the financial impact of an EV charging network data breach that is summarized in the next table.
In June 2023, a security researcher discovered an online database containing millions of logs (nearly a terabyte) of a global network of hundreds of thousands of EV charging stations in over 30 countries.
|
Financial Impact of an EV Charging Network Data Breach |
|||
| Impact | Description | Baseline | Financial impact |
| Vehicle safety, operations and recall | IBM offers a framework for cyber-based data breach costs and a benchmark for the average cost of a mega-breach (1 million or more compromised records) by number of records lost. The cost analysis includes direct and indirect costs associated with data breach detection, escalation, notification, post-breach response and lost business. | Average loss of $36,000,000 for data breaches that involve 1M to 10M records | $30,000,000 to
$40,000,000 |
| Legal and regulatory, compliance issues | GDPR Enforcement Tracker Report shows average fines for transportation and energy sectors, as well as insufficient technical and organizational measures to ensure information security. | Expected average fines in transportation sector (€864,776) and insufficient measures (€1,346,050) | $1,000,000 to
$2,500,000 |
| Total financial impact | Incident severity: high; Threat type: black hat; Breach size: 1 TB; Charging stations: 100,000+ | In 30+ countries | $31,000,000 to
$42,000,000 |
|
(Data source: Upstream Security, 2024 Cybersecurity Report) |
|||
The internal database, hosted on one of the most popular public cloud platforms, required no password to access and contained sensitive data of customers who used the EV charging network. Data contained names, email addresses, phone numbers of fleet customers, names of fleet operators with vehicles that recharge using the network, vehicle identification numbers and locations of EV public and private-residential charging points.
Emerging impact of GenAI in cyberattacks
The age of generative AI (GenAI) is emerging in the automotive industry, with many OEMs adopting GenAI capabilities to enhance product features and realize internal productivity and efficiencies. The emerging and potential future impact of GenAI in cyberattacks is a two-edged sword, as both negative and positive factors will happen.
GenAI is expected to become a key tool for black hat actors by assisting them to complete large-scale attacks and reduce barriers to entry. Black hats can apply large language models (LLMs) to quickly identify vulnerabilities and understand how to exploit them. This will give the black hats standard tactics, methods and processes for attacking CVEs.
GenAI can be used to map CVEs, target APIs and identify potential vulnerabilities, and provide step-by-step guidance to exploit vulnerabilities. LLMs can be used to generate malicious code or scripts by assimilating information from public vulnerability databases and cybersecurity research. APIs are especially susceptible, as attackers can use GenAI to explore API documentation, which may be publicly available, accidentally self-disclosed or leaked on the dark web.
From the use of GenAI to simulate attack environments, the automotive cybersecurity industry faces additional challenges, as it leads to more unpredictable and sophisticated attacks. GenAI will also increase the difficulty of detecting these attacks.
The good news is that GenAI also has the potential to transform automotive cybersecurity solutions and operations. GenAI will enable a range of use cases—from agile investigations and automating vehicle Security Operations Center (vSOC) workflows to generating complex insights based on deep and dark web data and in-depth Threat Analysis and Risk Assessment (TARA). Upstream is a leader in implementing GenAI in vSOC and other cybersecurity products and services.
GenAI greatly increases efficiency by enabling cybersecurity teams to quickly analyze massive amounts of connected vehicle and mobility data across multiple sources. GenAI can detect patterns, filter incident alerts and automate investigations. The automotive cybersecurity industry must embrace GenAI’s transformative capabilities against advanced threats from black hats using their own GenAI technology.
Summary
Automotive cybersecurity is a growth business on multiple levels—from vulnerabilities, number of attackers and attack sophistication to the response activities of the automotive cybersecurity industry players.
Several technology trends are making a significant impact, with SDVs adding a lot of software code that will have their share of vulnerabilities. AI technology is destined to become a major factor for cybersecurity attacks and for discovering, analyzing and defending against a flood of sophisticated attack vectors.
The growing use of social media as a breeding ground and distribution channel for malicious cybersecurity information is a worrying trend that will need attention from many players.
The diversity of cybersecurity attack vectors continues to grow. The many backend servers for telematics, connected car apps and mobility apps have become the largest attack vector, at 43% of all cyberattacks in 2023. Infotainment remains a common target due to the increasing amount of content and apps being used by more systems and devices.
A big vulnerability growth factor is the APIs that are used to communicate between different software platforms and apps and everything software-related. API-based communications are used billions of times per month, and a minuscule percentage of vulnerabilities can add up to major problems very quickly.
The cost of fixing and recovering from successful automotive cyberattacks is increasing quickly. The examples Upstream listed ranged from $17 million to nearly $50 million. Future costs will increase as the number of compromised vehicles grows.