Beware! Threat Actors Selling RDO Access on Hacker Forums
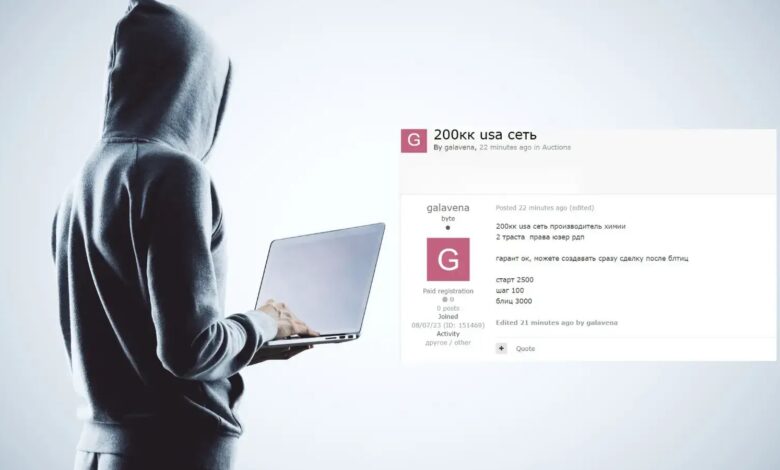
Cybersecurity communities are on high alert as threat actors have begun selling Remote Desktop Protocol (RDO) access on underground hacker forums.
This alarming trend poses significant risks to individual and organizational cybersecurity, potentially allowing unauthorized access to sensitive information and critical systems.
According to a recent tweet from Dark Web Informer, threat actors sell access to RDO (Remote Desktop Protocol) on hacker forums.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The Mechanics of the Threat
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that allows users to connect to another computer over a network connection.
In the hands of legitimate users, RDP is a powerful tool for remote administration and support.
However, in the wrong hands, it can serve as a gateway for cybercriminals to install malware, steal confidential data, or gain control over critical infrastructure.
The sale of RDO access typically involves credentials that include IP addresses, usernames, and passwords of vulnerable or compromised systems.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.
These credentials are often obtained through various means, such as phishing attacks, credential stuffing, or exploiting vulnerabilities in the RDP setup itself.
The availability of RDO access on hacker forums is not just a problem for the affected systems but poses a broader threat to cybersecurity.
It enables various malicious activities, from ransomware attacks to extensive data breaches.
Organizations whose RDP credentials have been compromised might not be aware of the breach until significant damage occurs.
Steps to Mitigate the Risk
To combat this growing threat, cybersecurity experts recommend several key practices:
- Ensuring that RDP access is secured with strong, unique passwords and, wherever possible, multi-factor authentication.
- Implementing strict access controls and monitoring logs for unusual access patterns.
- Keeping all systems updated with the latest security patches to mitigate vulnerabilities.
- Using virtual private networks (VPNs) to encrypt RDP traffic.
The sale of unauthorized RDO access on hacker forums highlights the ever-evolving landscape of cyber threats. Organizations and individuals alike must remain vigilant and proactive in their cybersecurity practices to protect against these insidious attacks.
As the digital world grows more interconnected, robust cybersecurity measures become increasingly paramount.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide



