Cybersecurity Vulnerabilities Increasing at the Operations Technology Level

The cybersecurity threat landscape for manufacturers and industrial control users shifted in 2021. Highly sophisticated threat groups and state actors deployed malware into manufacturing industrial control systems and, in essence, bypassed traditional defense-in-depth security strategies. The game-changing attack was the Pipedream malware attack in 2022, and one of the reasons why it has been successful, according to a Dragos report, is the homogenous control infrastructure in manufacturing. Global manufacturers are in the midst of the move to digital platforms, and recent malware attacks have targeted programmable logic controllers (PLCs) and even added arbitrary node attributes to an OPC-UA server, a network protocol used across all industries.
Attacks on operations technology (OT) are a big deal. While IT departments employ air gaps between corporate networks and OT systems, threat groups are finding access points via hardware and software inside plants. Dragos, a cybersecurity platform provider, released its 2023 OT Cybersecurity Year in Review report earlier this year and its seventh report overall. CEO and Founder Robert Lee expanded on the report’s findings via a webinar in February.
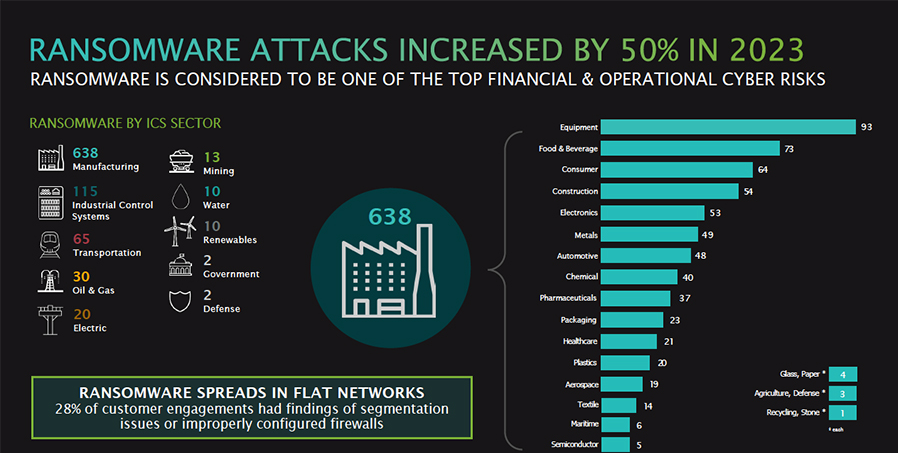
The 2023 report provides a deep dive on malware and OT attacks by industry, common vulnerabilities, insights from respondents, lessons learned from Dragos’ customer engagements, common vulnerability scoring system (CVSS) ratings and how ransomware attacks increased by 50% in 2023. This report is based on anonymous customer data, and Lee stresses the commonality of platforms in the modern manufacturing industries.
“We’ve already shifted to a homogenous world where most industries are now using common operating platforms, operating systems and network protocols,” Lee says. “Modbus TCP is everywhere, OPC-UA, and Codesys software inside of controllers (across all industries).”
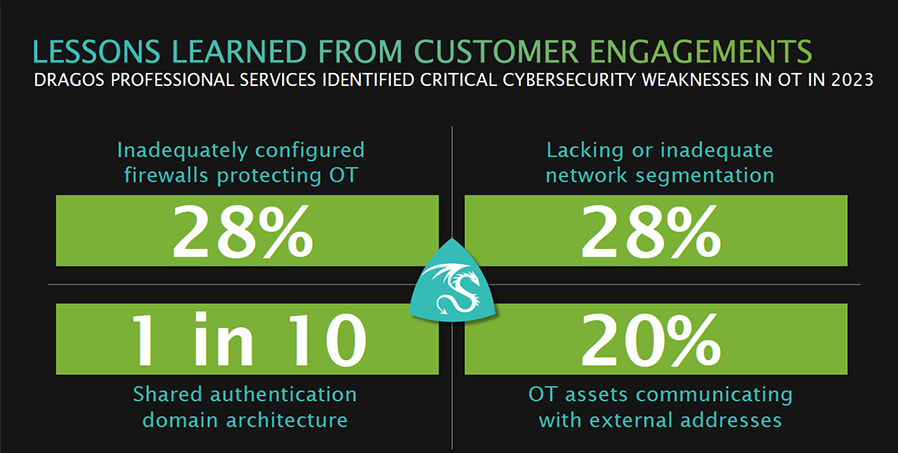
While the discussion centered on the shift toward managed detection and response (MDR), which Claroty, Dragos and others offer, the report’s lesson-learned section touches on network segmentation between IT and OT and some of the failures in this area. According to the 2023 report, 28% of its customers had an inadequately configured firewall protecting its OT environment, and another 28% lacked traditional network segmentation. For the latter, 20% of all OT assets were communicating with external addresses—communication to the Internet.
These vulnerabilities led to an increase in malware attacks in 2023. The Dragos report revealed that the food and beverage sector ranked second with 73 attacks within the overall manufacturing sector of its customers, while the equipment sector led with 93 attacks.
“When improperly configured firewalls and companies put such a large focus on segmentation, this is when security control fails,” says Lee. “When we looked at that shared active directory, this is the number one reason ransomware gets into operations environments. The compromise happens, rides that shared services area and attacks the OT environment.”
MDR is a relatively new frontier for many plant and operations food and beverage professionals in the OT space. “It’s very common to hear customers say I want to have threat monitoring and vulnerability management,” says Alexandre Peixoto, cybersecurity business director at Emerson. “I want to do penetration testing and all sorts of more advanced types of services or solutions.”
Peixoto divides customers into two camps when it comes to cybersecurity approaches: cyber-for-protection and cyber-for-convenience. Cyber-for-protection includes traditional defense-in-depth approaches between IT and OT networks. “For these customers, the most important consideration for cybersecurity is to defend their control systems against a potential cyberattack which could lead to an OT process upset,” says Peixoto.
According to Peixoto, cyber-for-convenience customers are employing defense-in-depth strategies but also trying new technologies—like MDR in OT environments—and are open to zero-trust security framework strategies.
According to Emerson, both customer types are asking how to navigate cybersecurity. Dragos’ Lee says real-world data helps “prove out” malware and monitoring technology to plant floor personnel. “When I started in the community years ago, there wasn’t really a data-driven report about what was happening in industrial control systems or operation technology; it was just anecdotal,” says Lee.
Dragos states detection response is best against malware frameworks, like Pipedream in 2022. “It’s not like a vulnerability that somebody can patch. It’s taking advantage of native functionality in these operation systems,” says Lee. “Anything with modern-day control systems from the last decade-plus, those systems can be manipulated and, if the physical environment allows for it, destruction.”
Emerson believes this is an urgent issue for customers and continues to be a trusted partner in control platforms and cybersecurity. “Pipedream is a toolkit for hackers,” says Peixoto. “For example, if an asset owner uses OPC UA communication protocol with their control systems in the way it’s designed, they could be potentially vulnerable if a hacker takes advantage of Pipedream.”
Emerson sees cybersecurity in OT as an opening for conversations with customers on a range of solutions. Emerson has a range of partnerships with well-known cybersecurity and networking companies, like Dragos, Nozomi Networks, Trellix, Belden, Thales, Acronis, OPSWAT and more.
“Recently, a customer said let’s do a pilot, and I want the bill of material today for a zero-trust implementation,” says Peixoto. “Zero trust is not a ‘thing’ yet, being a principle, we need to focus on the steps to go through a journey that targets a zero-trust implementation with a long-term strategy instead.”
While there is no standard zero-trust technology toolkit for OT, Lee recommends monitoring equipment with Internet connections and “east-west” traffic within OT networks and equipment.
“There’s still a lot of internet-connected industrial equipment out there or right behind an access point,” says Lee. “So make sure you’re being proactive. One of the best ways to be proactive in the OT environment is searching for connections coming out (of OT), not just viewing from corporate IT and into OT.” Via the report, Dragos cites 23 threat groups in 2023—and three new ones in 2024—and the company identified activity in the water sector and a brewery in November 2023: Full Pint Brewery in Pittsburgh.
Lee adds that the three new groups are explicitly targeting industrial environments in the U.S. “My concern is that as these types of state capabilities proliferate and follow that same path as Pipedream, and then we have Pipedream-light capabilities (that will target industrial OT),” says Lee. “So then making it accessible to people (threat actors) who don’t even have industrial experience, and that’s not obviously ideal.”
Hardening Equipment and CSecurity Partnerships
Besides threat monitoring and detection, automation vendors are hardening PLCs and to increase security. Siemens helped “cofound the Charter of Trust, a cross-business category to help combat the lack of security in digital enterprises and the digital economy as a whole.” Partners include equipment companies like Bosch and Mitsubishi to computing and cloud technology partners, such as Microsoft, Atos and Dell.
The Charter of Trust partnership also includes insurance companies, which are pushing food and beverage executives toward insurance policies and indirectly to National Institute Security Technology standards (NIST)—or the zero-trust framework. To qualify for insurance policies, manufacturers need to adhere to the NIST principles of assuming breach, which leads to more managed detection and response (MDR) solutions.
Moreover, Siemens and Emerson are hardening their control platforms via IEC standards. Siemens has successfully implemented a Secure Product Development Lifecycle under IEC 62443, Part 4-1 that has been certified by TuV, while Emerson received in 2019 the first system certification, for the DeltaV distributed control system (DCS), under IEC 62443 Part 3-3, after also having received its Secure Development Lifecycle Assurance under IEC 62443 for DeltaV’s development processes.
“We take security by design principles very seriously,” says Peixoto. “This is not a light effort; it involves a lot of reviewing code and checking for vulnerabilities on an ongoing basis.”
More Cybersecurity Threats in Operations
Claroty, a managed detection cybersecurity company based in New York City, recently addressed the specific issue of attacks against PLCs. A new white paper from Georgia Tech’s Georgia Institute of Technology (GIT) researchers presents new vulnerabilities due to web-based applications embedded in modern PLCs.
The paper, entitled “Compromising Industrial Processes Using Web-Based Programmable Logic Controller Malware,” discusses “a new technique that avoids known means of attacking PLCs via firmware vulnerabilities or modifications of control logic,” says Ryan Pickren, founder at BugPoC and co-author of the white paper, on the Nexus podcast Pickern discusses how this new research opens the door to attacks against PLCs that previously were accessible only to advanced attackers.
In their research attack, IronSpider, the GIT researchers exploited “commodity web vulnerabilities to access the web server’s control panel and either disrupt an automation process, damage industrial equipment and possibly endanger operators.” The import of all this ties into the malware intrusions cited by Dragos into OT environments. Pickern and GIT emphasize the web-based management of PLCs via handheld devices that are replacing traditional non-html human-machine interfaces (HMIs) on food and beverage plant floors, especially in larger operations.
“Now you get web visualization files that are modern HTML5 JavaScript GUIs, and that’s what’s been used to replace the HMI,” Pickren says. “Embedded web servers have technically been around for a while, but they’ve only recently become interesting.”
Pickren adds that his team’s attack would be difficult to detect because the traffic looks like standard web traffic cross-origin from a browser; all of it would look like standard API usage.
Beside MDR vendors like Claroty and Dragos, PLC vendors like Siemens are also moving into managed detection technology with its SIBERprotect. This MDR technology impedes the spread of cyberattacks and shortens the response time before defensive actions are taken and limits damage to plants. “The software can ingest cyberattack detection messages in syslog or CEF syntax and then immediately provide local plant notification, network quarantine,” says Chuck Tommey P.E., GICSP, ISA cyber expert. “It can integrate with automation systems to help put the system in an ideal state.”
With the addition of more MDR technology, companies are seeing more abnormal data activity on their networks. So how should companies respond to the threat analytics via their software?
“Across the 900 attacks (Dragos customers), there were about 50 different ransomware variants, and 25% of them were lockbit. So our advice to people is not to chase every indicator compromise,” says Lee. You’re just not going to be able to keep up.”
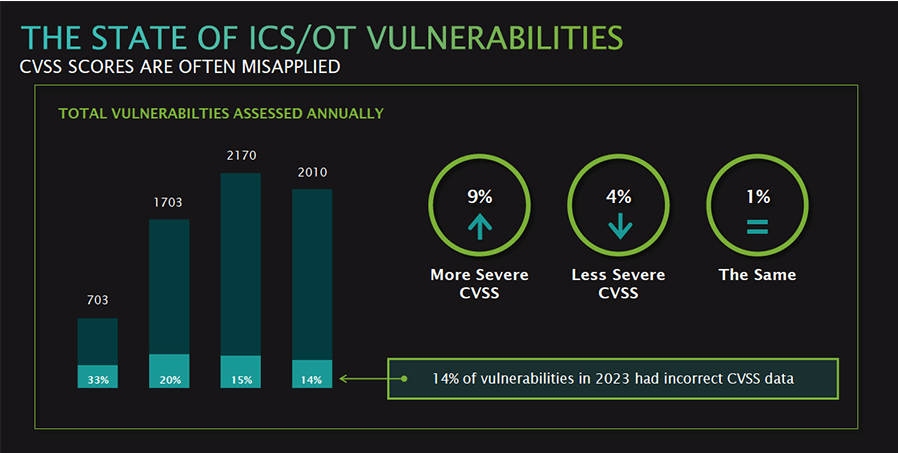
The webinar also discussed vulnerabilities and advisories publicly shared within the manufacturing, energy and healthcare segments. Dragos reviews common vulnerabilities scoring system (CVSS) ratings each year. A CVSS rating system is usually based on a score from 0 to 10 and is based on the severity of the vulnerability—RWE, Amazon and Philips Healthcare use these ratings. The Dragos report indicates that 9% of the time, CVSS scores that a vendor applies were higher or more severe than the advisory stated.
“What that means is the company publishing the advisory messed up the scoring, and 9% of the time, it was more severe than the vendor,” says Lee. “Four percent of the time, it was less severe, and then on percent, it was kind of exactly the same on that view. So, 14% of vulnerabilities in 2023 had incorrect CVSS.” Lee adds that using CVSS to prioritize those vulnerabilities might not be the best way.
To download and read the 2023 Dragos report, visit the company’s website.


