Materiality Issues in SEC Cybersecurity Disclosures | Kovrr
Over the past few decades, cyber attackers have increasingly wreaked havoc on the market, taking advantage of newer, more sophisticated ways to exploit system vulnerabilities. However, in fear of losing competitive advantages, organizations had notoriously downplayed the impact of these attacks, misleading investors and resulting in stock prices that did not accurately represent the risk landscape.
In response to these reporting discrepancies, the US SEC issued upgraded cybersecurity reporting regulations in July 2023, intent on creating a standardized disclosure framework and promoting a higher level of transparency. As of December 2023, public corporations are required to submit annual 10-K Forms that include cyber risk management processes and 8-K Forms, disclosing any materially impactful cyber events.
However, given its ambiguous nature, the materiality threshold, defined only as the level at which there is a “substantial likelihood that a reasonable shareholder would consider [it] important,” has caught many organizations off-guard. Indeed, in a recent market survey from AuditBoard, it was found that less than half of organizations have established processes and frameworks to determine such impact statuses.
This lack of preparedness, coupled with the recent slew of conspicuously detail-lacking 8-K submissions, many of which blatantly ignore the benchmark of materiality, signifies the need for more concrete definitions and guidelines. Only by providing this clarity can the SEC ensure disclosures include the consistent data necessary for keeping investors informed and the market stable.
What Is the Purpose of the SEC’s Cybersecurity Form 8-K?
While SEC-registered companies have been required to submit Form 8-Ks in the wake of a cyber attack for several years, the updated July 2023 regulations now mandate stricter reporting rules. For instance, organizations must disclose cyber incidents within four business days after they have been determined as material, thus eliminating any “unreasonable” delays.
The tougher disclosure rules also require that the affected registrant include the “nature, scope, and timing of the [material] incident” and any other information, both quantitative and qualitative, that could sway a reasonable investor’s decisions. Ultimately, the 8-K serves as a safeguard, ensuring such investors and market stakeholders remain fully aware of any cyber activity that could materially degrade their returns.
Reporting Non-Materially Impactful Cyber Events on the 8-K (H2)
Although the SEC specifically states that Item 1.05, the new component of Form 8-K regarding material cyber incidents, should only be submitted after an event has been determined to meet the respective materiality threshold, a significant proportion of organizations have disclosed prematurely. In fact, these entities have explicitly expressed the opposite, declaring that, despite public disclosure, business executives do not consider the cyber event to be material.
Public corporations including, but not limited to Hewlett Packard, UnitedHealth, Prudential Financial, and Cencora Inc. have all included the following text, in one form or another, in their respective 8-K disclosures:
“As of the date of this filing, the incident has not had a material impact on the Company’s operations, and the Company has not determined the incident is reasonably likely to materially impact the Company’s financial condition or results of operations.”
Plainly, there is a disconnect between what the SEC intended registrants to disclose and what’s actually occurring. This incongruity highlights the need for more specific guidelines to be issued that offer solid parameters for when an 8-K submission is necessary compared to when it’s not.
Why Are Organizations Submitting 8-Ks for Non-Material Cyber Events?
Despite being legally unnecessary, a string of recent events has likely prompted organizations to disclose immaterial incidents to the SEC. Most notably, Tim Brown, former SolarWinds Chief Information Security Officer (CISO), was charged by the commission with fraud for allegedly submitting misleading statements regarding the organization’s cybersecurity posture.
While Brown’s alleged misdeeds were not directly related to the latest cybersecurity disclosure regulations enacted in December 2023, the SEC’s move nevertheless sent a clear message throughout the cybersecurity community. No matter its form, the agency is ready and willing to take action against noncompliance.
Consequently, company stakeholders have decided that disclosing cyber events as a preventative measure would be in their best interests in terms of both legal and reputational protection. The logic in this situation is that there’s less risk in submitting unwarranted 8-Ks than later being found to have not submitted one if the cyber event turns out to have been materially impactful.
Lacking Crucial Details Regarding the Nature of Materiality
Another issue SEC registrants are having in regard to disclosing the apparently elusive “material” cyber event is being able to describe their methodology for deeming such incidents to be materially impactful. The most glaring example of this insufficiency appears in V.F Corporation’s Form 8-K, submitted two days after suffering from unauthorized system access.
Although the apparel company explicitly stated that “the incident has had and is reasonably likely to have a material impact” on business operations until recovery, they offered little more detail. In fact, the only information provided, qualitative in nature, that may be considered as an explanation for the materiality determination is that the “Company’s ability to fulfill orders [was] impacted.”
The SEC’s Response to V.F. Corporation’s Glaring Lack of Information
In the feedback stage of the SEC’s new cybersecurity regulations, many industry professionals expressed dismay at the shortened reporting deadline, claiming four days is not enough time to make a materiality determination nor include all of the relevant details. The SEC acknowledged this challenge and, in the final rulings, prescribed that if the initial 8-K submission was incomplete, organizations could submit another one four days later with more specifics.
However, according to the SEC, V.F. Corporation’s sparse 8-K did not even meet the minimum compliance requirements, and the commission argued that the lack of detail provided was unacceptable. In a follow-up correspondence, the governmental agency demanded that the registrant expand its disclosure by further describing both the scope of impacted operations and the known material impacts.
They also offered specific advice on how to do so: “For example, consider vendor relationships and potential reputational harm…as well as any impact on your financial condition.”
One day after receiving this letter, the company filed an amended 8-K with much more detail, including a quantified data record loss benchmark, more substantially explaining why it considered the December attack to be materially impactful.
The Problems With Under-Detailed and Non-Material Form 8-K Submissions
Under-Detailed 8-Ks
8-K disclosures that lack sufficient detail defeat the SEC’s underlying goal to protect investors by supplying them with consistent information regarding the effects of cyber events. When organizations fail to provide the data necessary for making informed decisions, stakeholders are unable to assess the full brevity of the situation and, therefore, its potential impact on returns.
Furthermore, under-detailed submissions leave more compliant competitors in the position of potentially suffering from their transparency, an act that should theoretically be rewarded. This inconsistency and lack of clarity not only undermine investor confidence but also hinder the market’s ability to price risk accurately.
Non-Material 8-Ks
Disclosing non-material cyber events on Form 8-Ks creates unnecessary noise in the market. Not only does this divert attention away from truly significant cyber events, but it also has the potential to lead to regulatory fatigue and complacency. Inundated with too many disclosures, stakeholders may become desensitized and fail to recognize or react appropriately to truly material incidents.
Developing Clearly Defined Materiality Thresholds With a Basis Point of Revenue
The materiality of a cyber incident can be determined by a wide range of factors, including the duration of the event, the number of records compromised, the extent of financial loss, as well as more qualitative elements such as reputational damage. Ultimately, “material” is a contextual concept defined according to the specific organization that has suffered an attack.
However, with such a broad scope for interpretation, many corporations evidently don’t know how to start the material determination process, let alone develop a comprehensive framework for doing so. This uncertainty leads them to disclose when unnecessary or provide unsubstantial information on their 8-K forms.
Before the unintended market consequences of these reporting discrepancies emerge at scale, the SEC needs to prescribe more concrete guidelines for materiality determination. One of the most straightforward means of doing so is to establish loss thresholds based on a percentage of an organization’s revenue. If losses exceed that amount in the wake of an attack, the company should seriously consider deeming it material.
These thresholds would not be considered absolute; they would not be the single determinant factor when deciding whether or not an incident should be classified as material. Rather, they offer an objective, dividing value that communicates whether or not an 8-K may be necessary in the first place and, therefore, a clear explanation for the SEC.
Quantifying Internal Loss Preliminary Benchmarks to Ensure SEC Compliance
Unfortunately, despite the reporting inconsistencies, the SEC is unlikely to take such a bold approach to develop a more concrete definition of and framework for determining materiality. Nevertheless, in an age when suffering from a cyber event is more a matter of when than if, organizations would do well to adopt this approach.
Preliminary quantified loss benchmarks offer business leaders data-driven insights that can be used to sharply define materiality, thereby ensuring reporting efficiency, consistency, and compliance. Leveraging these figures ensures that organizations only make disclosures when appropriate, keeping stakeholders aware and updated with details required for informed investment decisions.
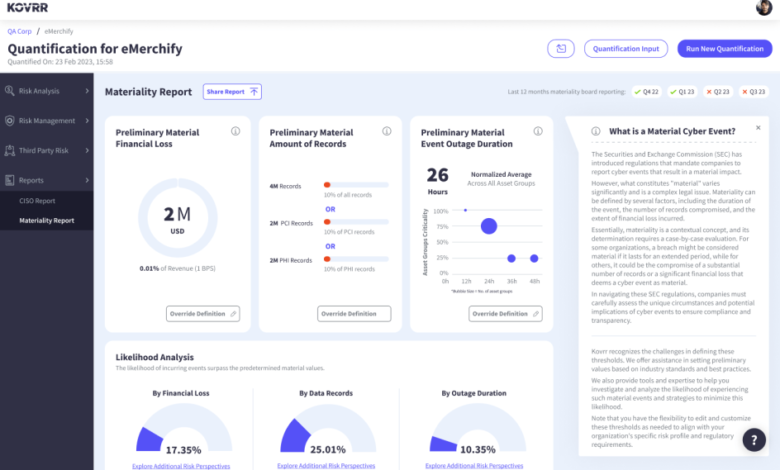
Kovrr’s Cyber Materiality Report
Kovrr’s cyber quantification risk experts conducted a comprehensive analysis of corporations worldwide and concluded that the best practices for determining materiality indeed begin with a basis point of revenue. Harnessing this research, Kovrr created the Cyber Materiality Report specifically to help organizations determine thresholds and disclose materiality.
To learn more about this one-of-a-kind offering that streamlines SEC reporting and compliance, you can download a sample report or schedule a free demo with one of our cyber risk management leaders.