Next-Gen Cybersecurity Strategies to Know

Next-generation cybersecurity is a strategy that employs cutting-edge tools, technologies, and frameworks to shore up your organization’s defenses. Read on to learn how to build your next-gen cybersecurity posture.
Increasingly Sophisticated Threats Call for Nex-Gen Cybersecurity
In today’s digital ecosystem, businesses’ threat landscape has evolved into a relentless and sophisticated battleground where cyber adversaries lurk around every virtual corner.
Every time we read something online or use an app, two cyberattacks happen somewhere in the world—at a rate of one attack every 39 seconds. Industry experts predict that data breaches could cost the global economy more than $9 trillion in 2024. From nation-state actors to cybercriminal syndicates on the dark web, malicious entities are armed with advanced tools and techniques to penetrate even the most fortified defenses.
Cyber-attacks come in various forms, ranging from ransomware assaults crippling operations to stealthy data breaches compromising sensitive information. The proliferation of interconnected devices through the Internet of Things (IoT) further expands the attack surface, providing hackers with numerous entry points to exploit.
Moreover, the rise of remote work has introduced new vulnerabilities as employees access company networks from unsecured devices and networks.
The consequences of a successful cyber-attack are catastrophic – encompassing financial loss, reputational damage, and legal repercussions. Beyond immediate impacts, the long-term ramifications can be severe, eroding customer trust and undermining business viability.
Businesses must recognize that traditional security measures are inadequate in the face of these evolving threats. They must adopt a proactive stance, implementing robust cybersecurity strategies prioritizing threat detection, incident response, and employee education. Failure to adapt to the complexities of the modern threat landscape is not an option, as the stakes have never been higher.
What Are the Key Components of a Next-Generation Cybersecurity Solution?
A next-gen security solution will incorporate 10 discrete components to create a resilient bulwark for your company and its digital assets. These include:
1. AI-powered threat detection
It’ll utilize artificial intelligence and machine learning algorithms to analyze data in real time, identifying patterns indicative of malicious activity before they can cause any real harm. This proactive approach guarantees early detection and mitigation of emerging threats before they escalate.
2. Zero trust architecture
Moving away from the traditional perimeter-based security model, it implements strict access controls and authentication mechanisms at every network level. This ensures that no entity –inside or outside the network – is inherently trusted. So, you can significantly reduce the risk of unauthorized access and lateral movement by attackers.
3. Endpoint security
Comprehensive endpoint security solutions go beyond traditional antivirus software. This component of next-gen cybersecurity will include endpoint detection and response, application whitelisting, and behavior-based analysis. Through a multi-layered approach, it safeguards endpoints against a wide range of threats, including malware, ransomware, and fileless attacks.
4. Cloud security
With the increasing adoption of cloud services and infrastructure, new security measures are essential to protect sensitive data and workloads. Next-generation solutions give you centralized visibility and control across cloud environments. You can leverage tools like cloud access security brokers (CASBs) and encryption to enforce policies and mitigate risks.
5. Identity and access management (IAM)
Taking off from a bedrock zero-trust, you must strengthen authentication and authorization processes with IAM solutions. This prevents unauthorized access to sensitive resources. Next-generation IAM platforms support adaptive authentication, multi-factor authentication (MFA), and identity governance to restrict access to privileged accounts and data.
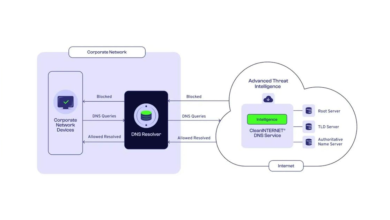
6. Threat intelligence integration
Threat intelligence feeds from reputable sources can provide invaluable context about emerging threats and attacker tactics. Next-generation cybersecurity solutions leverage this component to enrich detection capabilities, prioritize alerts, and inform incident response efforts. It enables your organization to stay one step ahead of its adversaries.
7. Security automation and orchestration
Next-gen cybersecurity solutions will streamline and automate security processes through orchestration platforms. This increases efficiency and responsiveness, allowing security teams to detect, investigate rapidly, and remediate threats. By linking different security tools and workflows, automation reduces manual effort and accelerates incident response times.
8. User awareness training
Recognizing that human error significantly contributes to cybersecurity incidents, next-generation solutions prioritize user awareness training programs. These initiatives educate employees about common threats, phishing techniques, and best practices for maintaining security. It empowers them to become the first line of defense – not the weakest link.
9. Continuous monitoring and compliance
These frameworks allow organizations to maintain a proactive security posture while adhering to regulatory requirements. They offer real-time visibility into network activity, vulnerabilities, and compliance status. This lets you ensure timely risk management and audit readiness.
10. Incident response and threat hunting
Next-gen solutions incorporate incident response playbooks, automated workflows, and advanced analytics – to organize effective response efforts and identify hidden threats lurking within the network. Such robust incident response processes and hunting capabilities are essential to mitigate the impact of cyber-attacks.
Innovative Cybersecurity Strategies for a Hyperconnected World
As you prepare your business and its security perimeters for an age of hyper-connectedness and digital proliferation, here are the next-gen security strategies that can help:
- Cyber-physical security fusion: Integrate cybersecurity with physical security measures to protect interconnected systems and devices, such as Industrial Control Systems (ICS). This approach ensures comprehensive protection against both cyber threats and physical intrusions.
- Deception technology: Deploy decoy assets and deceptive techniques to mislead and divert attackers away from critical infrastructure and data. You can neutralize threats in real time while gathering valuable intelligence about attacker tactics and objectives.
- Threat-intelligence sharing platforms: Participate in collaborative intelligence platforms to exchange real-time threat intelligence with industry peers and security vendors. These platforms facilitate collective defense efforts.
- Cyber resilience training: Simulate realistic cyber-attack scenarios and empower employees to effectively recognize and respond to threats. Hands-on training exercises enhance awareness across the organization, reducing the likelihood and impact of successful attacks.
- Cyber insurance with risk-based pricing: Partner with providers offering risk-based pricing models informed by real-time intelligence and assessments. It’ll also incentivize you to improve your cybersecurity posture.
How to Implement a Robust Cybersecurity Framework in the Digital Age
To keep up with the needs of next-generation cybersecurity, you need to:
- Assess your current cybersecurity posture—Conduct a comprehensive assessment of your organization’s current cybersecurity capabilities, including existing policies, procedures, and technical controls. Through thorough risk assessments and security audits, identify potential vulnerabilities, gaps, and areas for improvement.
- Define your cybersecurity objectives and requirements — Clearly define your organization’s cybersecurity objectives, goals, and desired outcomes. Establish specific cybersecurity requirements based on regulatory compliance, industry standards, and best practices relevant to your business sector.
- Implement technical controls and security measures — Install and configure firewalls, intrusion detection and prevention systems (IDPS), antivirus software, endpoint security solutions, and secure email gateways to defend against common cyber threats. Implement encryption protocols, multi-factor authentication (MFA), and security information and event management (SIEM) solutions.
- Enable continuous monitoring and threat detection—Implement continuous monitoring tools and technologies to detect and respond to cybersecurity threats in real-time. Deploy SIEM, EDR, and threat intelligence platforms to promptly identify and mitigate security incidents.
- Establish incident response and recovery procedures — Set up a designated incident response team with clearly defined roles and responsibilities, including incident coordinators, technical analysts, legal advisors, and communications specialists.
- Conduct regular security assessments and audits — Perform regular security assessments, penetration tests, and vulnerability scans to identify weaknesses and potential security gaps in your organization’s systems and networks. Also conduct periodic security audits and compliance assessments.
- Stay informed and adapt to emerging threats — Stay abreast of the latest cybersecurity trends, emerging threats, and industry developments through continuous learning and professional certifications. Proactively adapt your cybersecurity strategy and controls to mitigate new threats.
- Engage with external partners and resources—Collaborate with trusted cybersecurity vendors, industry associations, and government agencies. This will help you access resources, guidance, and support. Consider outsourcing certain cybersecurity functions.
Selecting the Best Next Generation Cybersecurity Solution
Your choice of next-generation cybersecurity solution will hinge on a blend of diligence, foresight, and adaptability. Look for vendors with a track record of excellence, robust customer support, and a commitment to ongoing research and development.
Remember that cybersecurity is not a one-size-fits-all endeavor; the best solution aligns closely with your unique business goals and risk profile. By prioritizing innovation, collaboration, and a proactive mindset, you can empower your organization to navigate the complexities of the digital age with confidence and resilience.