Strength in Unity: The Power of Cybersecurity Partnerships
In a recent conversation with Iren Reznikov, we discussed into the intricacies of aligning investment decisions with broader business goals and the pivotal role cybersecurity partnerships play in driving industry-wide innovation.
I recently had the opportunity of sitting down with Iren Reznikov, Director, Venture Investments and Corporate Development at SentinelOne. During our conversation–which you can listen to here–Iren shed light on the S Ventures approach to investment, emphasizing the importance of a forward-thinking mindset that drives the team to look beyond immediate gains and short-term objectives. Instead, they focus on long-term growth, strategically investing in emerging technology anticipated to be critical for SentinelOne’s sustained growth and relevance in the coming years.
Central to SentinelOne’s investment strategy is the recognition of the transformative potential of partnerships and collaborations. By fostering synergies between industry players, partnerships unlock new avenues for value creation and enhance the overall cybersecurity ecosystem.
Let’s explore how these joint ventures and strategic investments provide substantial benefits, driving innovation and delivering enhanced value to both companies and end users alike.
The Benefits of Partnerships in Cybersecurity
- Comprehensive Solutions: As Iren mentions, no single company can provide all the necessary tools and expertise to combat all cyber threats effectively. Even for established cybersecurity vendors like SentinelOne, partnerships form a pathway to leverage complementary expertise and accelerate the delivery of value to customers. This approach allows companies to pool their resources and expertise to create more robust and comprehensive security solutions. It also ensures that end users stay protected against diverse cyber threats with robust solutions that address network security, endpoint protection, cloud security, and more.
- Better Integration: According to an IBM study, 30% of respondents said their organizations deploy more than 50 security tools and technologies. Joint technologies often result in better-integrated security solutions that work more seamlessly together. For customers, this means easier deployment, management, and maintenance of security systems, leading to a more user-friendly experience and reducing the complexity of managing multiple security products.
- Innovation Acceleration: Collaboration fosters innovation by bringing together different perspectives, skills, and technologies. By combining resources and expertise, partners can innovate more quickly and adapt their solutions to meet changing needs.
Rather than focusing solely on immediate gains, the S Ventures team adopts a visionary perspective, identifying spaces that will be strategically significant three to five years down the line. This forward-looking mindset serves as a compass, guiding their investments toward areas poised to shape the cybersecurity landscape of tomorrow.
“…From my perspective, one of the most important ways to foster innovation is through partnerships because when you think about it, even if you’re a big cybersecurity company and you have a broad platform and you’re developing tons of products like SentinelOne, you can’t develop everything at the same time.
You want to make sure that you’re creating the right partnerships with companies that you believe in, and you think that there is a value in partnering with them to give that value to your customers. So, you can do that easily through partnerships and it’s not time consuming, it’s not resource consuming when you’re doing the right partnerships with the right companies.”
Iren Reznikov, SentinelOne
- Global Reach: Cybersecurity threats are not confined by geographic boundaries. Many organizations operate on a global scale or have customers and partners in multiple countries. Partnering with firms that have a global presence allows companies to extend their cybersecurity capabilities across different regions and industries.
Noetic Cyber and SentinelOne: A Prime Example of Complementary Security Solutions
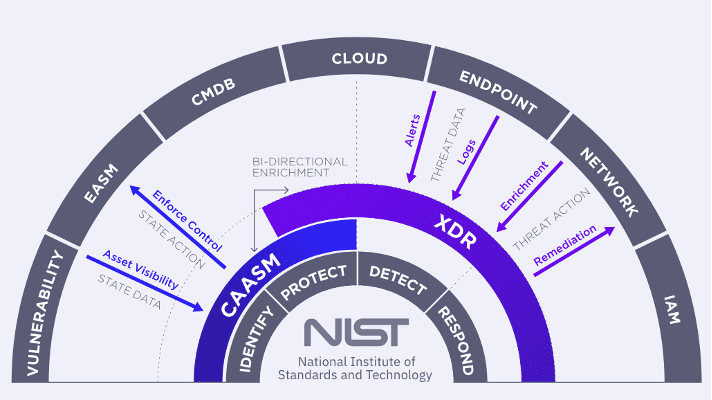
Integrating Extended Detection and Response (XDR) with Cyber Asset Attack Surface Management (CAASM) exemplifies how together, complementary security technologies can enhance each other’s value. CAASM solutions depend on security data from different tools for asset intelligence, and XDR serves as an excellent source of data through its native endpoint, identity, and cloud telemetry.
Learn more: Extended Detection and Response & Cyber Asset Attack Surface Management to Achieve Greater Security Coverage
Conversely, CAASM solutions can enrich XDR response workflows with detailed asset intelligence, offering improved context and prioritization. This data includes information on asset exposure, criticality, and the potential impact if compromised. By leveraging the strengths of both XDR and CAASM, organizations can achieve a more comprehensive and proactive approach to cybersecurity, ultimately improving their ability to detect, respond to, and mitigate threats.
Through their strategic investments and collaborations, S Ventures ensures that SentinelOne remains at the forefront of technology advances, continuously adapting to new challenges and opportunities. This proactive approach not only enhances SentinelOne’s competitive edge but also fosters a culture of innovation and agility within the organization. By aligning their resources with emerging trends and partnering with industry leaders, S Ventures enables SentinelOne to anticipate market shifts and swiftly respond to the evolving cybersecurity landscape—ultimately resulting in sustained growth, resilience, and a robust capability to protect customers against sophisticated threats.
*** This is a Security Bloggers Network syndicated blog from Noetic: Cyber Asset Attack Surface & Controls Management authored by Alexandra Aguiar. Read the original post at: https://noeticcyber.com/cybersecurity-partnerships-iren-reznikov/



